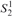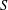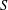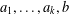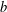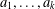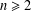Refine search
Actions for selected content:
46 results
The complexity of intersecting subproducts with subgroups in Cartesian powers
- Part of
-
- Journal:
- Glasgow Mathematical Journal , First View
- Published online by Cambridge University Press:
- 07 October 2025, pp. 1-7
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Complexity of Faceted Explanations in Propositional Abduction
-
- Journal:
- Theory and Practice of Logic Programming , First View
- Published online by Cambridge University Press:
- 05 September 2025, pp. 1-19
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Keeping your distance is hard
-
-
- Book:
- Games of No Chance 6
- Published online:
- 18 May 2025
- Print publication:
- 05 June 2025, pp 433-446
-
- Chapter
- Export citation

Proof Complexity Generators
-
- Published online:
- 29 May 2025
- Print publication:
- 26 June 2025
Chapter 4 - Primer
- from Part I - Background
-
- Book:
- Working with Network Data
- Published online:
- 06 June 2024
- Print publication:
- 13 June 2024, pp 39-62
-
- Chapter
- Export citation
The atomic properties of stress
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Dyadic Existential Rules
-
- Journal:
- Theory and Practice of Logic Programming / Volume 24 / Issue 2 / March 2024
- Published online by Cambridge University Press:
- 24 August 2023, pp. 227-249
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Exact convergence analysis for metropolis–hastings independence samplers in Wasserstein distances
- Part of
-
- Journal:
- Journal of Applied Probability / Volume 61 / Issue 1 / March 2024
- Published online by Cambridge University Press:
- 05 June 2023, pp. 33-54
- Print publication:
- March 2024
-
- Article
- Export citation
Implicit computation complexity in higher-order programming languages: A Survey in Memory of Martin Hofmann
-
- Journal:
- Mathematical Structures in Computer Science / Volume 32 / Issue 6 / June 2022
- Published online by Cambridge University Press:
- 15 March 2022, pp. 760-776
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
EXPLORING THE LANDSCAPE OF RELATIONAL SYLLOGISTIC LOGICS
- Part of
-
- Journal:
- The Review of Symbolic Logic / Volume 14 / Issue 3 / September 2021
- Published online by Cambridge University Press:
- 21 October 2020, pp. 728-765
- Print publication:
- September 2021
-
- Article
- Export citation
DECIDING SOME MALTSEV CONDITIONS IN FINITE IDEMPOTENT ALGEBRAS
- Part of
-
- Journal:
- The Journal of Symbolic Logic / Volume 85 / Issue 2 / June 2020
- Published online by Cambridge University Press:
- 16 June 2020, pp. 539-562
- Print publication:
- June 2020
-
- Article
- Export citation
Deciding the Existence of Minority Terms
- Part of
-
- Journal:
- Canadian Mathematical Bulletin / Volume 63 / Issue 3 / September 2020
- Published online by Cambridge University Press:
- 24 October 2019, pp. 577-591
- Print publication:
- September 2020
-
- Article
-
- You have access
- Export citation
16 - Fast Gamblet Transform
- from Part III - The Banach Space Setting
-
- Book:
- Operator-Adapted Wavelets, Fast Solvers, and Numerical Homogenization
- Published online:
- 10 October 2019
- Print publication:
- 24 October 2019, pp 297-344
-
- Chapter
- Export citation
9 - Reasoning about Generic ω-Sequences
-
- Book:
- The Metaphysics and Mathematics of Arbitrary Objects
- Published online:
- 24 May 2019
- Print publication:
- 13 June 2019, pp 162-188
-
- Chapter
- Export citation
CONSISTENCY PROOF OF A FRAGMENT OF PV WITH SUBSTITUTION IN BOUNDED ARITHMETIC
-
- Journal:
- The Journal of Symbolic Logic / Volume 83 / Issue 3 / September 2018
- Published online by Cambridge University Press:
- 23 October 2018, pp. 1063-1090
- Print publication:
- September 2018
-
- Article
- Export citation
A GENERAL POSITION PROBLEM IN GRAPH THEORY
- Part of
-
- Journal:
- Bulletin of the Australian Mathematical Society / Volume 98 / Issue 2 / October 2018
- Published online by Cambridge University Press:
- 18 July 2018, pp. 177-187
- Print publication:
- October 2018
-
- Article
-
- You have access
- Export citation
Connectivity in Hypergraphs
-
- Journal:
- Canadian Mathematical Bulletin / Volume 61 / Issue 2 / 01 June 2018
- Published online by Cambridge University Press:
- 20 November 2018, pp. 252-271
- Print publication:
- 01 June 2018
-
- Article
-
- You have access
- Export citation
ON SEMIGROUPS WITH PSPACE-COMPLETE SUBPOWER MEMBERSHIP PROBLEM
- Part of
-
- Journal:
- Journal of the Australian Mathematical Society / Volume 106 / Issue 1 / February 2019
- Published online by Cambridge University Press:
- 30 May 2018, pp. 127-142
- Print publication:
- February 2019
-
- Article
-
- You have access
- Export citation
When you must forget: Beyond strong persistence when forgetting in answer set programming*
-
- Journal:
- Theory and Practice of Logic Programming / Volume 17 / Issue 5-6 / September 2017
- Published online by Cambridge University Press:
- 30 August 2017, pp. 837-854
-
- Article
- Export citation
Precise complexity guarantees for pointer analysis via Datalog with extensions*
-
- Journal:
- Theory and Practice of Logic Programming / Volume 16 / Issue 5-6 / September 2016
- Published online by Cambridge University Press:
- 14 October 2016, pp. 916-932
-
- Article
- Export citation