Introduction
There are schools of thought in international law regarding where the methodological emphasis should lie. These vary from practitioner to practitioner and sometimes from issue to issue. The members of one such school are sometimes colloquially called “jurisdictionalists” because they tend to the view that, despite the temptation to analyze international law problems as “realists” or “diplomats,” or to take into account the various political aspects of any given matter, many legal issues between states are best approached from the standpoint of jurisdiction — specifically, those international law rules that govern how, when, and where states may exert their sovereign power. So doing, it is argued, allows one to identify problems in the most legally sound manner and provides the best platform from which to propose solutions, even though the solutions themselves may very well involve realism, realpolitik, or diplomacy. It also acknowledges that the rules around jurisdiction arise from the nature of state sovereignty and are, in fact, a primary manner in which states channel their sovereign power vis-à-vis other states.
To analyze otherwise is to put the cart before the horse; it is simply more efficient to begin with jurisdiction than to attack the problem from the standpoint of, say, what is most advantageous to a particular party to the problem or to focus on the subject matter of the issue. Beginning with jurisdiction draws a frame around the picture, which can then be filled in by using the other colours on our palette. While many might disagree on the primacy of this particular tool bag in a broad sense, the jurisdictionalist point of view is at its most powerful when examining legal issues that arise in the context of transnational criminal law. Footnote 1 State sovereignty concerns are at their stickiest and most intense when the criminal law is engaged, and, thus, jurisdiction becomes a most useful lens for analysis when looking at how states cooperate — or fail to cooperate — in the suppression of transnational crime.
In my view, the current furor around the Microsoft Ireland case Footnote 2 wending its way through the US courts bears the hallmarks of a discussion that has fallen into the traps that jurisdictionalists seek to avoid. The case has been fervently discussed and blogged upon in many interested communities, but it can be summarized quite simply. Footnote 3 In a criminal investigation US federal prosecutors identified a user’s email account held by Microsoft and wished to obtain both the account’s content and any metadata associated with it. A New York magistrate issued a warrant directing Microsoft to produce the content (including emails) and associated metadata. Footnote 4 While it produced the metadata, which was stored in the United States, Microsoft moved to quash the warrant on the basis that the rest of the data was stored in Ireland and, thus, beyond the jurisdictional reach of the US government. The motion to quash was dismissed by the magistrate, and Microsoft voluntarily placed itself in contempt of the order for the warrant in order to advance the case to the Second Circuit Court of Appeals. Footnote 5 A number of amici filed briefs in the Second Circuit, which heard oral argument in September 2015 and rendered its decision in July 2016 (discussed below). The issue, simply put, is whether it is lawful for a government to compel an individual within its territory to produce data that is stored on the territory of another state, even if the individual in question has the technical ability to retrieve and produce the data.
The Microsoft Ireland case is significant in part because it appears to be the first case on this particular issue that has approached a major appellate court in a common law jurisdiction, or at least the first where the international law aspects of the question have been explicitly raised. Footnote 6 Parenthetically, it may not be the last, as Google is embroiled in a similar dispute before the federal courts in a different district. Footnote 7 On a broader view, however, this development is a very current splash in an already roiled pond. It is a specific example of the challenges posed by the increasing amount of digital evidence that must be gathered in transnational crime cases Footnote 8 and of the way that these challenges are fraying the fabric of traditional models of cooperative evidence gathering used by states. Traditionally, the bar on extraterritorial enforcement jurisdiction (explained in more detail below) has meant that states that resorted to gathering evidence beyond their territories did so at their own legal peril, and, in recent decades, mutual legal assistance treaty (MLAT) practice has developed to serve this need. Footnote 9 However, gathering digital evidence (whether it is in servers located in known locations in other states or in “the cloud”) presents both opportunities and challenges — opportunities because of the relative ease with which evidence can be obtained via computer, but challenges because of state reluctance to allow foreign enforcement authorities to pierce territorial borders, even where those borders are straddled by cyberspace.
Part of the reason why the Microsoft Ireland case, in particular, is clouding the waters of this discussion is that a great deal of the conversation revolves around American law, particularly American procedural and constitutional law and the manner in which that state’s law interacts with international law (the presumption against extraterritoriality when interpreting statutes, the “Charming Betsy” doctrine, and so forth). Footnote 10 The result of this has been that the international law issues at the heart of the case are not always clearly understood — for example, the clear distinction between extraterritorial prescriptive and enforcement jurisdiction (described below) is sometimes lost. Many of the commentators who do go into the international law issues nonetheless give them short shrift, often referring away the issue as “the MLAT problem” and using it as a springboard for proposals involving a new and/or different approach to how law enforcement operates in this area. While all of that will definitely play a role in the resolution of the case itself, the goal here is to analyze the problem from a strictly international law point of view, with domestic laws and practices utilized simply as examples of state practice rather than assuming any normative role on their own. This is a more modest goal than attempting to figure out how to resolve the problem, but it may be that generating a solid international law understanding of the issues will help in the generation of solid solutions.
Extricating the discussion from the morass of US law and law enforcement policy concerns that surround it is useful, in my view, for two reasons. First, as explored below, the precise legal issue at play in the Microsoft Ireland case is not a new one, but it is one that is assuming increasing importance between states engaged in transnational criminal cooperation, and a picture of the international scene could be of some use. In the end, despite the frustration with the nature of the international legal system that moves commentators to demand we “do something different,” international law is ultimately a consent-based system, and a positivist approach provides the clarity needed for the formulation of solid legal alternatives. Second, the time is right for a more internationally focused, and thus less United States focused, examination of these issues, particularly as they involve the storage of data. It has been correctly observed that in terms of where international user data is located, “at the moment, US-based providers dominate much of the global market and US law and practice therefore impacts on a significant percentage of international internet users.” Footnote 11 However, the legacy of the Edward Snowden/Wikileaks disclosures regarding US surveillance practices appears to be a shift away from the US market as the default location for the data centre market, Footnote 12 as demonstrated by the “data sovereignty” movement seen in some states Footnote 13 and by the relocation of data centres by Internet companies themselves to jurisdictions where there is greater legal protection for privacy and where, at least for the moment, there is a shield of territorial sovereignty to be wielded (a feature of the Microsoft Ireland case itself). Footnote 14
The remainder of this article will proceed in four parts. The second part will briefly review the fundamental international jurisdictional principles that form the backdrop for any discussion of cross-border evidence gathering, particularly the bar on extraterritorial enforcement jurisdiction and the tools that have been crafted to allow for criminal cooperation between states. The third part will examine the specific jurisdictional challenges to cross-border electronic evidence gathering in transnational crime cases, Footnote 15 in particular, the seizure of cross-border electronic evidence by police, and assess the overall “lay of the land” in terms of international law norms. The fourth part will look at the specific problem raised by the Microsoft Ireland case — that of courts or prosecutorial authorities ordering private parties to produce digital evidence that is located in a foreign state — and will attempt to ascertain whether it is indeed a problem of extraterritorial enforcement jurisdiction or a different species of problem altogether. The fifth part will offer the quite unstartling conclusion that the problems associated with the issue in the Microsoft Ireland case specifically, and with cross-border evidence gathering more generally, are jurisdictional in nature, and jurisdictional problems are best resolved by treaties or other forms of cooperative arrangement. It will also comment on the utility of proposals to stretch the boundaries of the otherwise “hard law” prohibition against extraterritorial evidence gathering, proposals suited to a world in which electronic evidence is becoming central.
Jurisdictional Fundamentals
“Jurisdiction,” in the international law sense used here, is “the term that describes the limits of legal competence of a State … to make, apply and enforce rules of conduct upon persons.” Footnote 16 In international law, the jurisdiction of states is generally considered to be an aspect of state sovereignty, and the rules surrounding the exercise of jurisdiction by states are meant to manage potentially conflicting sovereign interests. States being territorial entities, conflict is less likely when states exercise jurisdiction entirely within their own territories. Thus, it is situations where a state’s exercise of jurisdiction somehow extends beyond its territory — usually referred to as extraterritorial jurisdiction — that the international law of jurisdiction is designed to address. As has been noted,
[t]he international law regarding the exercise of jurisdiction by states can be expressed simply: one state’s exercise of sovereign power cannot infringe upon the sovereignty of another state or states. This is easy enough to assert, but nebulous and nuanced in application because judging where the line is crossed is a complex exercise. ... [T]he rules differ as between [prescriptive] and enforcement jurisdiction … The central point of conflict will be situations of concurrent jurisdiction; that is, where two or more states have some legal claim to exercise jurisdiction over a particular matter. Footnote 17
The Lotus case tells us that states being sovereign entities, they are free to exercise jurisdiction in any way they choose, barring a rule to the contrary. Footnote 18 There being no ab initio prohibition on the exercise of jurisdiction, the international law rules are essentially designed to manage and head off potential conflict or, as it has been phrased, “to safeguard the international community against overreaching by individual [state]s.” Footnote 19
The key distinction is the one named in the excerpt quoted above between prescriptive jurisdiction (the ability of states to make laws pertaining to people, places, and things) and enforcement jurisdiction (the ability of states to apply or enforce those laws). Extraterritorial law-making by states tends to be considered lawful when it extends along one of the familiar traditional principles of jurisdiction: nationality, passive personality, protective, and universal. This generally permissive approach is in stark contrast to the rules surrounding the exercise of enforcement jurisdiction. The latter can for present purposes be understood as the ability of a state to enforce its criminal law not just through the prosecution in court of individuals but also through the ability of police to exercise the powers (often compulsory) required for the investigation of crimes, what the Supreme Court of Canada has labeled “investigative jurisdiction” — search and seizure, witness/accused questioning, arrest, and so on. Footnote 20 Enforcement jurisdiction is strictly territorially bounded; in the oft-quoted words of the Lotus case, a state
may not exercise its power in any form in the territory of another State. In this sense jurisdiction is certainly territorial; it cannot be exercised by a State outside its territory except by virtue of a permissive rule derived from international custom or from a convention. Footnote 21
Accordingly, the police of State A cannot go across the border into neighbouring State B and arrest an individual, nor can they exercise other police powers, at least without the consent of State B.
The ban on extraterritorial enforcement jurisdiction is fairly straightforward and tends to be viewed restrictively and enforced strictly by states. It is important to appreciate the contours of how the rule works and how it interacts with the rules about prescriptive jurisdiction, all of which can be illustrated by simple, but true-to-life, examples:
-
• X commits murder in Canada and flees to the United States. Canada can exercise prescriptive jurisdiction over the crime, but cannot exercise enforcement jurisdiction over the person.
-
• Z, an American, commits murder in Oregon and flees to British Columbia. Canada can detain or arrest the person (on the basis of a request from the United States), but has no jurisdiction over the crime.
-
• Y, a Canadian, commits a terrorist crime in France and returns to Canada. Canada has extraterritorial prescriptive jurisdiction over the crime (on the basis of nationality), but can only exercise enforcement jurisdiction over the person because he is in Canada.
-
• The same scenario as immediately above involving Y and his return from France to Canada, but, in their investigation, Canadian police wish to gather forensic evidence and interview witnesses, all of which would occur on French soil. They are prohibited from this exercise of extraterritorial enforcement jurisdiction, even though Canada has jurisdiction over the crime and the person.
The latter point is a particularly important one because it is sometimes argued (as, indeed, the US government argued in Microsoft Ireland) that if a court has both “subject matter” and “personal” jurisdiction then it may issue whatever orders it wishes involving the case. This terminology is largely lifted from private international law and does not reflect the strictness of the international law prohibition on extraterritorial enforcement jurisdiction. To wit, a state may have jurisdiction over both the crime and the person, but this does not give it the ability lawfully to gather the evidence on its own because that evidence is in the territory of another state.
States tend to be quite chauvinistic about their domestic criminal laws and, thus, guard their sovereignty closely in this arena. Footnote 22 In fact, the international law of jurisdiction is generally understood to have evolved from state practice around conflicts of criminal law. Footnote 23 Conflicts between states over the exercise of criminal jurisdiction are by no means ordinary, but they do occur, and the investigation of any transnational criminal matter is meant to be shaped by sensitivity to the prohibition on extraterritorial enforcement jurisdiction. After all, enforcement activity on a state’s territory that is not sanctioned or even known about by that state undermines the entire rule of law in that state and, in particular, any human rights protections. It is important not to understate the dangers presented by jurisdictional conflict since, as one experienced commentator has noted,
[s]tates and intergovernmental organizations act with caution, deliberation and consensus because the consequences of precipitous unilateral actions can be dire. The First World War started, in part, because one State insisted on the right to conduct a criminal investigation into the murder of one of its officials on the sovereign territory of another. Footnote 24
Less calamitously, breaches of the rule against extraterritorial enforcement jurisdiction can create legal and diplomatic complications between states, create havens for criminals in situations where extradition is interfered with, and, perhaps most seriously, can compromise the level of trust that is required for states to cooperate in the suppression of transnational crime. In the Canadian experience, such breaches have led to both extradition Footnote 25 and mutual legal assistance requests Footnote 26 being denied by courts as well as the corrosion of relationships between Canadian and US police forces. Footnote 27
Over the past century and a half, the increasing need to combat transnational crime has moved states to craft tools to allow them to provide mutual cooperation in crime suppression while, at the same time, respecting the jurisdictional rules and the sovereign interests they protect. Extradition, then, is properly understood as a formal (indeed, treaty-based) agreement by a state to exercise enforcement jurisdiction on its own territory (by way of arrest, detention, and rendition) on behalf of its partner/requesting states on a reciprocal basis. Similarly, under mutual legal assistance treaties, states are obliged to exercise various other forms of enforcement jurisdiction (typically investigation-type activities) on their territories, again on the request of treaty partners. The treaties themselves have a dual function: they create the legal obligation between the states, and they provide (via implementation) a basis in domestic law for the enforcement activities that the requested state carries out. Footnote 28
INTERPOL, while predominantly an information-sharing network among national police forces, serves a similar function with its Red Notices, under which states can arrest and detain individuals who are outside the territory of the state that wants them. More recently, there has been a growth in the use of more direct policing cooperation, utilizing such mechanisms as posting liaison officers in foreign states, joint investigation teams, and “shiprider” agreements Footnote 29 on bilateral, multilateral, and regional bases. Footnote 30 These are employed with varying degrees of formality, but they have taken on extra layers of formality and obligation as they are used by regional organizations such as EUROPOL and form a significant part of the undergirding of the more recent transnational criminal law suppression conventions. Footnote 31 Importantly, all of this activity is done with an eye to guarding the sovereignty of all states involved, particularly the state that is the locus of the investigation: “[I]t is traditional to apply limiting conditions so as to ensure that investigative activities in state B conducted by or on behalf of state A will comply with state B’s laws, norms, and traditions.” Footnote 32
By way of illustration, Canadian practice bears this out on both sides of the coin; in R v Hape, for example, Royal Canadian Mounted Police officers were engaged in a cooperative investigation with police in Turks and Caicos, but were bound strictly by the laws of that territory and under the authority of local police, pursuant to an agreement that was in place. Footnote 33 Under the terms of the Canada–United States Framework Agreement on Integrated Cross-Border Maritime Law Enforcement Operations, each state’s enforcement officers are assimilated to those of the partner state and, when operating in the partner state, possess only those powers that the partner state’s officers can exercise. Footnote 34
Cross-Border Electronic Evidence Gathering
APPLYING THE PROHIBITION ON EXTRATERRITORIAL ENFORCEMENT TO ELECTRONIC EVIDENCE
The foregoing section was a fairly conventional account of the international law of jurisdiction but was necessary to underpin the discussion here — in no small part because it is important to understand that the rules that exist evolved during times when investigation and prosecution of crimes occurred in the physical (or, as some prefer it, “kinetic”) world. The remainder of this article is about the uneasy interaction between these rules, the presence and nature of digitized information, and shifting state interests and abilities in criminal investigation.
As communication technologies have come to play a more and more ubiquitous role in crime, as in life, there has been a corresponding increase in the preoccupation with how law enforcement can effectively and efficiently gather electronic data for use as evidence. Footnote 35 Due to the form it takes and how it exists within the international communications infrastructure, electronic evidence has a naturally “transnational” nature, and it is increasingly clear that traditional, territorially bound jurisdictional norms such as those described above obstruct investigation more than was even the case with traditional, kinetic evidence. Yet, the early prediction of cyberspace as some kind of “separate place” that could have its own independent legal regime died on the vine. As will be seen, states do treat the Internet and the overall international communications infrastructure as a territorially bounded place, and technology continues to develop in such a way that allows them to do so. Footnote 36 The goal of this section is to review the international law norms regarding enforcement jurisdiction as they apply to cross-border electronic evidence gathering, and it could properly be quite short, as study after study over the last decade or more have indicated that states view cross-border intrusion by law enforcement authorities as a breach of sovereignty and a violation of the bar on extraterritorial enforcement jurisdiction. Footnote 37 Unpacking this picture provides a more nuanced, but still firm, view on this point.
Electronic evidence, in the form of digitized material, presents enforcement challenges for a number of reasons, but most importantly because it is ephemeral and subject to easy movement and manipulation by computers. Accordingly, the question of enforcement jurisdiction regarding electronic evidence very quickly becomes one about “jurisdiction over the Internet” since Internet-based access to the data is really the heart of the matter. If a police officer seizes a computer, a server, a compact disc, or a thumb drive full of data in a foreign state and then drives across the border to her own state, that is essentially the same kind of enforcement jurisdiction as an unlawful search and seizure in traditional terms and can be understood and dealt with in the same way. However, if a police officer who is in a foreign state causes data to be electronically compelled and sent across borders or, more pressingly, if police officers operating computers in their own state obtain data that is stored in a foreign state, the problem becomes more complex. Data can be transient and fast moving; its actual geographical location can be uncertain; and real-time monitoring and gathering may be needed or even required to successfully take an investigative step. The data may be openly obtainable by a website fully accessible to anyone via the Internet, it may be protected by law but not security measures, or it may be secured and require electronic intrusion of some sort (“hacking”) to obtain. Whatever the territorial or geographical aspects of a particular matter, the Internet — and its use by criminals — is the locus of the problem.
Perhaps the single greatest dashed hope regarding the Internet was that it would prove to be a place sui generis, apart from the kinetic world, free from regulation by state laws Footnote 38 or, alternatively, that it would function as some sort of res communis space, subject to cooperative and collective regulation under international law. Footnote 39 None of these Latin hopes ever took shape. From reasonably early times, states could and did treat the Internet as a territorially bounded place. Footnote 40 Jurisdiction was asserted and assumed over as broad a range of state interests as could be imagined, from crime to private law torts, to commerce, to speech, to culture. Footnote 41 As Bert-Jaap Koops and Susan Brenner comment in the preface to their edited collection of studies on jurisdiction over cybercrime, “territoriality still turns out to be a prime factor; apparently, cyberspace is not considered so a-territorial after all.” Footnote 42
To be sure, the Internet has caused notable and significant stresses and stretching effects upon the jurisdictional rules. As Teresa Scassa and I explored in an earlier article, Footnote 43 the assertion of prescriptive jurisdiction by states over Internet-based activities has led to a rise in the use of the “qualified territoriality” or “extended territoriality” principle — the assertion of jurisdiction based on the impact of a matter upon the territory of a state, even if the whole matter was not contained within that state’s territory. Footnote 44 This principle has proven useful in allowing states and regulatory authorities to deal with the fact that Internet-based matters do not correspond easily to Westphalian concepts. As Justice Gerard La Forest famously said regarding crimes, they may occur “both here and there.” Footnote 45 Yet this is a simple stretching of the territorial principle to deal with the practical realities that globalization has wrought and one that fits well (if slightly fuzzily at its margins) within the traditional law of jurisdiction.
State practice regarding enforcement jurisdiction has also remained more conservative in regard to electronic evidence and generally reflects a territorial understanding of how the law will treat the gathering of data by law enforcement — a view buttressed in no small part by the fact that technological developments increasingly make it possible to tell where data is present or stored. Footnote 46 A recent piece on cybercrime sums up the prevailing attitude of states:
International law is clear that, while offences may be given extraterritorial application to protect essential interests, any form of extraterritorial investigation or enforcement requires the consent of any country on whose territory it takes place. This includes any kind of investigative measures … and without consent, foreign investigative measures would be fully subject to local criminal laws. Foreign intrusions would also usually be regarded as an infringement of sovereignty calling for some sort of retaliatory action. Footnote 47
This statement captures the findings of numerous studies that have been done on the subject in the last fifteen years. Indeed, expressions by states of the dual concern of maintaining state sovereignty over territory while coming up with an effective approach to deal with the problem can be tracked back to the 1980s. Footnote 48 The case most frequently cited to prove the point is that of Gorshkov/Ivanov, Footnote 49 two Russian cybercriminals who hacked numerous websites and stole large amounts of information, including credit card numbers. The two were lured to California by the Federal Bureau of Investigation (FBI) under the guise of a job interview at a technology company, and during the “interview,” FBI agents monitored Gorshkov’s access to his computer back in Russia. Obtaining his login and password information, the agents accessed his computer and downloaded its entire contents in order to collect evidence with which to prosecute. Russia protested this action as a violation of its territorial sovereignty and charged the FBI agents with hacking, the Russian Federal Security Service explicitly invoking territorial sovereignty as part of its overall objection. Footnote 50
This same view was quite evident in the negotiations leading to the Council of Europe’s Convention on Cybercrime, concluded in 2001. Footnote 51 It was clear that potential states parties to the treaty were keenly aware that the inherently cross-border nature of data meant that territorial borders were essentially getting in the way of effective investigation, but the official Explanatory Report also reflects that a territorial understanding of enforcement jurisdiction was still the dominant point of view and that consensus on solutions was difficult to achieve. Footnote 52 The only compromise reached was embodied in Article 32 of the convention, which permitted cross-border access to data by law enforcement authorities in either of two situations: (1) the data is “publicly available (open source)” and, thus, obtainable by anyone on the Internet or (2) the investigating state obtains the lawful and voluntary consent of a person who is legally entitled to disclose the data. Even this fairly mild compromise was controversial, as Slovakia has stated that notwithstanding the article it considers that its domestic courts must still approve any request for data, Footnote 53 while Russia highlighted the article as part of its reasons for not ratifying the convention. Footnote 54
These examples illustrate that states are sensitive and conservative about any cross-border electronic traffic by foreign investigators and that they wish to maintain the ability to object publicly to actual events or even potential intrusion. There are understandable policy reasons for this. The integrity of territorial sovereignty and control is always key in any discussion of inter-state interaction, and, as noted above, the criminal law is where states are at their most guarded. More specifically, a state may have dual criminality concerns and be leery of the potential for being unwittingly implicated in a prosecution of conduct that it does not view as criminal. It may wish to retain the capacity to refuse to cooperate or allow its territory to be used for enforcement activity where it would view the foreign prosecution (or some aspect of it) as contrary to its ordre public — for example, the pursuit of a political dissident under the guise of a criminal prosecution or the suppression of forms of speech that the target state views as being legitimate, to say nothing of the varied views among states on what constitutes terrorism. A permissive or unguarded position on cross-border data gathering deprives a state of this sovereign capacity and allows the investigating state “to circumvent such principles.” Footnote 55 Many states are also sensitive to the potential for depriving individuals of human rights protections in the form of procedural standards and would prefer that their own judiciaries or other authorities approve any evidence gathering on their territories. As the Transborder Group of the Cybercrime Convention Committee notes,
[e]veryone agrees that transborder access must protect individuals by setting conditions and safeguards on computer and network searches by law enforcement entities. However, States diverge in their views of what safeguards and protections should apply. Well-known examples include differences on the scope of freedom of expression or the requirements on police to obtain an order authorizing a search. The people in a particular State normally expect, at a minimum, the protections afforded to them by this State; they do not expect to be searched according to the standards of a State they do not live in and may never have been in. In turn, the State has an obligation to respect individuals’ rights and freedoms incorporated into its domestic law. Footnote 56
This issue has been studied a great deal, and the observation has been consistently made that, regardless of the investigational utility or the desirability of not imposing state borders on cyberspace for the purposes of enforcement jurisdiction, it is the overall view of states that this is what is required. Footnote 57 This has continued to be the case well after the early twenty-first-century examples described above. One of the most recent studies, by Bert-Jaap Koops and Morag Goodwin, sums things up nicely:
[T]he most solid view on what international law permits is that accessing data that are, or later turn out to be, stored on a server located in the territory of another state constitutes a breach of the territorial integrity of that state and thus constitutes a wrongful act (where the action is attributable to the state), except where sovereign consent has formally been given. Footnote 58
In its large-scale cybercrime study released in 2013, the United Nations Office on Drugs and Crimes’s inter-governmental expert group reached a similar conclusion, producing data that indicated that two-thirds of responding states view cross-border access to computer systems or data to be impermissible and (outside limited exceptional situations) requiring access to formal channels. Footnote 59 Even more recently, the United States and the United Kingdom — two powerful, technologically advanced states whose relationship of mutual trust is well known — began talks towards a treaty that would allow reciprocal direct access to both stored data and traffic data. The proposed treaty is explicitly intended to address the need for an alternative to MLAT procedures. Footnote 60 The norm, then, seems to be a hard one.
VARIATIONS IN STATE PRACTICE
It is important to return to methodology at this point. Since the prohibition on extraterritorial enforcement jurisdiction is properly viewed as a customary international law norm, then the foregoing represents primarily the opinio juris quotient. States have fairly evenly expressed the view that cross-border electronic data gathering by investigative officials is an unlawful exercise of enforcement jurisdiction. However, in the complex and fast-moving world of transnational crime cases involving data, state practice is not always consistent with this view of the norms. Viewed collectively, at least, there is a certain dissonance between what states say and what they do.
When using treaty-making and legal modeling as examples of state practice, then, additional support for the prohibitive norm is observable. Aside from Article 32 of the Convention on Cybercrime and the other state practices mentioned above, the Arab Convention on Combatting Information Technology Offences contains rules regarding transborder access that can allow one to infer that acting otherwise would breach the prohibitive norm, and similar deductions can be made from the Common Market for Eastern and Southern Africa Cybersecurity Draft Model Bill. Footnote 61 Moreover, the mere existence — let alone the increasing prominence — of MLATs is also at least indirect evidence of the norm.
Drilling down to the level of domestic laws and investigative activities that form state practice, however, reveals a more nuanced picture than the public attitudes of states would suggest. While not all of the data assembled on the issue necessarily tracks the formal legal positions of states, the observers who have been surveyed have noted that there is an uncertain, but significant, amount of unilateral cross-border electronic evidence gathering, or other enforcement activity, by police and security personnel. Footnote 62 Some of this is simply done unilaterally by the police officers involved, while, in other situations, it is accomplished by way of direct inter-police cooperation, but without the sanction of either judicial authorities or other government apparatus of the territorial state. It is not always documented. Footnote 63
On other occasions, the authorities of the territorial state are notified after the fact. Two Dutch cases are instructive. In the first, Bredolab, Dutch law enforcement determined that a foreign-located botnet had infected millions of computers worldwide, including a number of servers located in the Netherlands. The authorities took over the botnet and sent messages to every infected computer. Footnote 64 In the second, Descartes, Dutch authorities were investigating a TOR server containing child pornography that they suspected was located in the United States, and they notified American authorities about the server. When it was discovered that the server was actively posting newly made images, Dutch police copied the images for use in possible prosecutions, destroyed the images on the server, and blocked access to the server. The decision was made not to seek MLAT-based assistance because of time pressure, but the US authorities were later notified and provided with copies of the images seized; there was no objection from the United States. Footnote 65
Moreover, despite the overall tilt towards viewing such actions as sovereignty violations, a surprising number of states have laws that allow or even compel them. The controversial British Data Retention and Investigatory Powers Act of 2014 contained broad extraterritorial powers to compel data, including people and companies located outside the United Kingdom being compelled to disclose data relating to conduct outside the United Kingdom — by way of warrants served on them outside the United Kingdom. Footnote 66 It has even renewed this approach in more recent proposed amendments. Footnote 67 A study by the Cybercrime Convention Committee revealed that the laws of a number of Council of Europe states allow unilateral transborder access in various scenarios, including Belgium, Norway, Portugal, Serbia, and Romania. Footnote 68 There are similar laws in Singapore, Footnote 69 Australia, Footnote 70 and, at the time of writing, similar draft legislation in Ireland. Footnote 71 The US Department of Justice and the FBI have introduced amendments to Federal Rule of Criminal Procedure 41, which were recently adopted by the US Supreme Court, Footnote 72 authorizing search warrants that permit remote accessing of data in other states where the location of the data is not known. Footnote 73 Interestingly, the Department of Justice responded to concerns about potential sovereignty violation by pointing out that US law already permits such actions where the location of the data is known. Footnote 74
It is clear that the various imperatives that make cybercrime investigation difficult are presenting challenges to the more conservative traditional stance among states regarding extraterritorial enforcement, and, indeed, the theme of all of the literature on the topic tends to be along the lines of “we cannot do it that way any more, we need new tools.” The need for these new tools is made all the more acute by the fact that even knowing where the data is at any given moment can be difficult, due to big data companies using more fluid data storage techniques. Footnote 75 Yet the tension between investigational needs and the protection of sovereignty contributes to a sense of disarray that pervades the landscape. MLAT procedures, designed to deal with exactly this issue, are felt to be too blocky and time-consuming to be effective for investigation purposes — to the point that the US government has made the curious argument in the Microsoft case that it must be allowed to subvert these procedures because they are inconvenient. Footnote 76 Yet what is increasingly referred to as “the MLAT problem” is a real practical concern for law enforcement, and even the ramped-up cooperation regime in the European Convention on Cybercrime is not perceived to have helped matters much. Footnote 77
An alternative approach that initially met with some success was for police to make requests of Internet service providers, cloud storage services, and other data holders for voluntary disclosure of data, particularly in cases involving child sexual abuse and child pornography. While this is apparently lawful under Article 32 of the Convention on Cybercrime, it is deeply controversial both within and without the Council of Europe states, with many states and commentators taking the view that it is objectionable. Footnote 78 Nonetheless, it was and is a fairly popular practice, Footnote 79 and many of the “big data” companies have been content to comply with such requests, particularly in investigations regarding child sexual abuse or child pornography. However, this practice has begun to tail off of late, both because national courts such as the Supreme Court of Canada have blocked the practice Footnote 80 and because the ripple effects of the Wikileaks revelations have made companies more insistent on domestic search warrants or production orders based on MLAT requests. Footnote 81
What is the methodological result of this situation? In short, it appears that despite overall state insistence that unauthorized cross-border evidence gathering breaches the bar on extraterritorial enforcement jurisdiction, when it comes to electronic data, state practice does not match up evenly with the opinio juris. Whether and how the traditional norm applies to the newer practices is, at best, uncertain. Such a state of uncertainty creates the potential for conflict — for example, the approach of “better to seek forgiveness than permission” illustrated in the Dutch cases mentioned above may respond to law enforcement exigencies, but the reaction from a sovereignty protection point of view would not always be positive, and, of course, the purity of the objectives would not mitigate a claim of state responsibility for the investigating state. Moreover, what is clear is that the lack of unity on the legality of the practice means that due process and human rights concerns are often being neglected.
The Microsoft Ireland Issue
FRAMING THE PROBLEM
Having assessed how well or poorly the traditional norm covers active police cross-border data gathering, the next step is to examine the more indirect method that is raised by the Microsoft Ireland case. The methodological question, then, is this: can State A order Individual X to produce data that X controls, but that is stored in State B? Or, in the context of the case itself, can the US government order Microsoft to produce data that is stored in Ireland for use by the state in a criminal investigation? For the present purposes, this legal question will be referred to hereafter as the “Microsoft Ireland issue.”
It is first worth noting that this discrete legal issue becoming the subject of attention is a display of the adage “everything old is new again.” The question of whether it is a breach of international law for the courts of one state to compel private parties to disclose documents located in another state is one that well predates the popular use of either electronic data storage or the Internet. Beginning in the late 1960s, such orders issued by US courts in civil litigation matters involving transnational corporations were viewed as intrusive upon domestic sovereignty by the jurisdictions targeted, including Canada, the United Kingdom, France, and Australia — each of which enacted blocking statutes to prevent the companies from complying with the foreign orders. Footnote 82 Moreover, even today, the issue persists outside the cybercrime setting, as the advent of cloud storage has made it more difficult for companies involved in litigation to comply with court orders to disclose the contents of their cloud storage (or easier to refuse to comply, depending upon one’s perspective), due to concerns about infringing the laws or sovereignty of the state in which the cloud storage facility resides. Footnote 83
It is of interest that this issue has arisen once again in the US context, for as Google was at pains to point out in a recent filing in its own case on the issue, Footnote 84 the American government is well aware of the sovereignty issues at play, indications of which appear in sources such as the United States Attorneys’ Manual and a Department of Justice manual on obtaining electronic evidence. Footnote 85 An interesting recent (if implicit) recognition of the issue is a new practice used by US authorities in corporate criminal prosecutions: to offer cooperative credit to companies being prosecuted so that they will “voluntarily” produce documents that are in another jurisdiction. Footnote 86
This is not to say, however, that parties, courts, or governments who encounter the issue always recognize it. In the Canadian context, the most prominent case to have dealt with the kind of facts that might give rise to the Microsoft Ireland issue is eBay Canada Ltd v Canada (National Revenue), where revenue authorities invoked a section of the tax statute that provided for the compulsion of documents relevant to a tax assessment, even if they were located in another state. Footnote 87 The information sought existed in electronic form on eBay’s central servers in California and was easily electronically accessible to eBay Canada’s personnel. The Canadian office’s effort to resist the disclosure order was rebuffed by two levels of court, essentially on the basis that, since the data was so easily accessible, it was “formalistic in the extreme Footnote 88 to say that it was not actually in the possession of the Canadian company. The extraterritorial jurisdiction aspects of the disclosure order were avoided by this construction of the facts, though no true consideration was given to the international law issues or to the relevant state practice, perhaps because it was not raised by the parties.
As for Parliament, the Supreme Court of Canada noted in Tele-Mobile Co. v Ontario that the federal government had stated that it enacted production orders in the Criminal Code as a means of compelling individuals with possession or control over data located outside Canada to surrender it, so as to solve “the problem that has in part been created by inexpensive overseas data warehousing.” Footnote 89 The implicit position is clearly that jurisdiction over the individuals who possessed or controlled the data is sufficient jurisdiction to order its production. This measure was taken seemingly without much Footnote 90 consideration of whether it was consistent with international law or, indeed, without recognition that Canada itself had opposed such measures before US courts. Footnote 91
Also worth mentioning is the long-running struggle between the criminal authorities of Belgium and Yahoo, which began with a run-of-the-mill fraud investigation launched in 2007. Belgian authorities demanded that Yahoo produce Internet protocol addresses associated with email accounts that were implicated in the investigation, but Yahoo refused on the basis that it was not present in Belgium as it had no business infrastructure there and, thus, did not fall under Belgium’s territorial jurisdiction. At every stage of the proceedings, it argued that the appropriate manner for Belgium to gather the data was by way of a MLAT request. Footnote 92 In December 2015, the Cour de Cassation upheld lower court rulings against Yahoo, Footnote 93 on the basis that the broadcast of Yahoo’s services into Belgium gave it sufficient presence to base jurisdiction on the extended territoriality principle. Accordingly, Yahoo was required to respond to the request. The case appears to have proceeded on the assumption (similar to the Canadian position) that if Yahoo was within Belgium’s jurisdiction, the latter could lawfully demand production of the data, without any explicit consideration of the Microsoft Ireland issue. Footnote 94
To say that something is controversial or opposed in some examples of state practice is not, however, to say that the issue is settled. The Court of Appeals factums of the various parties and interveners in the Microsoft Ireland case display an interesting array of arguments that sketch out some of the major legal and policy angles. It is worth briefly reviewing some of these arguments for that reason, although the focus here will be on the international law issues rather than on the local legal peculiarities. Microsoft itself rested its argument essentially on traditional notions of extraterritorial enforcement jurisdiction: while the assertion of personal jurisdiction over the company and the actual act of disclosing the data to the government might occur on American soil, the execution of the warrant to retrieve the data happens in Ireland, where the data is stored, which amounts to extraterritorial enforcement. Even a proper interpretation of the relevant US statutes produces the conclusion that the MLAT procedure is the lawful route — not least because “in 2006, the US and EU negotiated … a self-executing treaty that expressly favours bilateral cooperation for data seizures, not unilateral intrusions into each other’s territory.” Footnote 95
Microsoft also pleaded that the case had already caused international discord, a proposition confirmed by both the record of the case and the public dialogue among the state players. Ireland filed an amici brief in the case clearly stating its view that its territorial sovereignty was implicated and that the case represented a potential infringement thereof. It also asserted that the matter was covered by the MLAT between the states and indicated its willingness to execute the MLAT process “as expeditiously as possible.” Footnote 96 Finally, it pointedly mentioned its own law to the effect that Irish courts might be empowered to “order the production of records from an Irish entity on foreign soil,” but would give great weight to whether the order would violate the law of the foreign state. Footnote 97
The European Union (EU) and the Council of Europe have taken even stronger postures. A brief was filed by Jan Philipp Albrecht, German member of the European Parliament and vice-chair of its Committee on Civil Liberties, Justice and Home Affairs. He criticized the lower court decision as having “endorsed the by-passing of the EU MLAT and the respect for foreign jurisdiction inherent therein,” his main pitch being that EU privacy protection standards are significantly higher than those of the United States, and, thus, avoiding the MLAT regime prevents the oversight required by European authorities in sharing data. Footnote 98 Moreover (and redolent of the earlier manifestations of this problem discussed earlier in this section), if the US court held that Microsoft must comply with the warrant, this would cause a conflict since EU laws would prohibit the transfer of data to the United States. Albrecht also noted that he was the European Parliament’s rapporteur for the current negotiations between the EU and the United States for a treaty on the protection of personal data in cooperative criminal investigations. Footnote 99 Upholding the warrant, he said, “would forestall this future agreement and disturb these negotiations.” Footnote 100 This view was supported by a letter from Vivane Reding, vice-president of the European Commission, in which she expressed the view that the magistrate’s decision in Microsoft Ireland “bypasses existing procedures,” is an exertion of extraterritorial jurisdiction that may breach international law, and causes companies to be caught in an untenable conflict of laws. Footnote 101 A similar stance was taken by the Council of Europe’s commissioner on human rights. Footnote 102
The best international law analysis was presented in the amici brief by Anthony Colangelo of Southern Methodist University’s Dedman School of Law, who supported Microsoft’s overall position but made a number of finer methodological points. He located the central problem as a matter of determining whether the warrant actually amounts to an extraterritorial action by the United States, a question he answered in the affirmative. He emphasized the principle of non-intervention, arguing that the warrant in question is an extraterritorial extension of enforcement jurisdiction into what is clearly a sovereign territorial interest of Ireland’s, despite the fact that the intrusion is electronic rather than kinetic. Footnote 103 Importantly, the question of extraterritoriality is not appropriately answered unilaterally, as the lower court did, but, rather, with due consideration of the interests and positions of the relevant states, and he submitted that great weight should be given to the views of both Ireland and the EU on this question. Finally, by circumventing the United States–Ireland MLAT, the procedure amounts to a breach of the treaty, specifically the “obligation to implement these agreements in good faith” under the Vienna Convention on the Law of Treaties. Footnote 104
The briefs of other interveners and amici made a number of a similar points as well as a host of arguments regarding the interaction of US law and international law that are not strictly relevant here. An important point made by a group led by the Electronic Frontier Foundation was that establishing this kind of warrant procedure as permissible could very well lead to foreign regimes with weaker data protection laws feeling emboldened to compel businesses with presences on their territories to surrender the personal data of American citizens Footnote 105 — a strong example of the kind of “tit for tat” response that generally makes states conservative about the manner in which they exercise extraterritorial jurisdiction. Footnote 106 A coalition of data firms made a similar point, giving the example of personal data of American human rights activists stored on American computers being turned over to the Russian government, a situation that illustrated the kind of “international free-for-all” that could result. Footnote 107
And the decision of the Court of Appeals? Given the amount of international law that was argued, the court’s reasons are quite anaemic, turning essentially on the difference between a warrant and a subpoena under the domestic legislation involved (the Stored Communications Act). Footnote 108 Having decided that the instrument in question was actually a warrant, the court construed the warrant as a very territorially limited species of state action to which the usual statutory interpretation presumption against extraterritorial application applied. This was particularly the case here, given that the Stored Communications Act contained no language indicating any congressional intent towards extraterritorial application. The court rejected the government’s argument that the order was in fact a kind of subpoena, although it cited its own and other US case law to the effect that a subpoena requiring an individual in the United States to produce documents held abroad was lawful, without any consideration of the lawfulness of that point under international law. Footnote 109
There was little international law analysis to speak of, other than the acknowledgement that the presumption against extraterritoriality was applied in order not to interfere with international relations. The factual apogee was the court’s recognition of two points: (1) that Irish territory was implicated and (2) that Microsoft gathering the data simply amounted to the government acting indirectly rather than directly:
[I]t is our view that the invasion of the customer’s privacy takes place under the SCA [Stored Communications Act] where the customer’s protected content is accessed — here, where it is seized by Microsoft, acting as an agent of the government. Because the content subject to the Warrant is located in, and would be seized from, the Dublin datacenter, the conduct that falls within the focus of the SCA would occur outside the United States, regardless of the customer’s location and regardless of Microsoft’s home in the United States. Footnote 110
The high water mark of international legal analysis arrived in the tail end of the majority’s decision, in which the court brushed up against the possibility that international law norms might be breached, though under the scope of “comity” rather than law:
Our conclusion today also serves the interests of comity that, as the MLAT process reflects, ordinarily govern the conduct of cross-boundary investigations. … [W]e find it difficult to dismiss those interests out of hand on the theory that the foreign sovereign’s interests are unaffected when a United States judge issues an order requiring a service provider to “collect” from servers located overseas and “import” into the United States data, possibly belonging to a foreign citizen, simply because the service provider has a base of operations within the United States. Footnote 111
Despite the fact that, as indicated above, the question of whether the warrant amounted to a breach of foreign sovereignty had been argued by the parties, the Court did not really entertain the question of whether there was a prospect of unlawful extraterritorial enforcement jurisdiction. Indeed, at several points in the judgment, there are indications that the distinction between prescriptive and enforcement jurisdiction was confused by both the government Footnote 112 and the court. Footnote 113
Accordingly, for all of the heated discussion around the case, it has thus far resolved very little from an international law point of view; a Supreme Court appeal might change that, but at the time of writing, none had been announced. At most, it is an example of state practice (by way of a court decision) from which it can be indirectly inferred that the state in question feels that the act might be unlawful. Much turned on the fact that warrants are treated more restrictively than subpoenas under US law, which in both practical and international law terms is a distinction without a difference — in each case, the government is compelling a party to surrender data located in the territory of another state. The issue remains the one being explored in this section: is this lawful under international law? Most important, then, is the court’s recognition that the execution of the warrant would take place in Ireland, despite being electronically initiated in the United States by a US company. As explored in detail above, this tends to be the position taken by states, and while the court did not refer to it, this view was reflected in the record. This point becomes more important in the actual international law analysis of the question, taken up the following section.
STATE PRACTICE
To the extent that the Irish and European positions expressed in the Microsoft Ireland case might be taken as expressions of opinio juris on the Microsoft Ireland issue, an examination of state practice reflects an even greater level of dissonance between opinio juris and state practice than is the case with the more general cross-border data seizure issue. In some cases, the dissonance is quite striking. For example, as mentioned above, while the United States and the United Kingdom are negotiating a treaty that will allow warrants for foreign-stored data to be executed, each has in place laws allowing the state to compel individuals within their territories to surrender data stored abroad; Footnote 114 and as also noted above, despite Ireland’s sovereignty-oriented posture in the Microsoft case, it admits it has the same kinds of mechanisms available. Footnote 115 While one might suspect that France would be amenable to the position expressed by the EU and European Commission officials, French courts recently asserted jurisdiction to order Twitter to produce data relating to anti-Semitic hashtags that violated French laws, Footnote 116 dismissing Twitter’s protestations that the data were stored in the United States. Footnote 117
Beyond these well-publicized incidents, actual practice relating to the Microsoft Ireland issue can be difficult to track, as it tends to be rolled into the overall cross-border data question in the literature. However, a useful paper produced by international law firm Hogan Lovells in 2012 surveyed the issue quite directly with regard to ten different states, Footnote 118 and some indications of other state practice can be found in the doctrinal literature. Footnote 119 A chart that provided a rough illustration of this available data on state practice, then, would look like this:
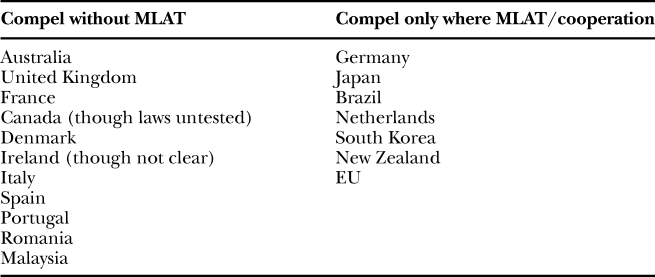
There is certainly a bipolar quality to this situation. As one commentator remarked on the similar topic of surveillance, “[i]n this environment, the same action in response to a surveillance directive may be at once both legally required by one government’s laws and legally forbidden by another’s.” Footnote 120
ANALYZING THE PROBLEM
In light of the foregoing, the most that can be said about the issue from a customary international law point of view is that the current landscape reflects the overall state of play on cross-border electronic evidence gathering more generally. While states generally take a territorial sovereignty point of view, there is a dissonance between what states say (opinio juris) and what they do (state practice). In order to properly analyze the problem, then, we must resort to first principles. In my view, there is a compelling argument that a state engaging in behaviour similar to that of the US government in the Microsoft Ireland case is in breach of international law, specifically the prohibition on extraterritorial enforcement jurisdiction.
This point of view can emerge from both factual and legal analysis. Factually, a private individual is being compelled by the state to obtain data that it owns, possesses, or controls, which is stored on the territory of another state. It is important not to fall into the “computers are different” fallacy and remember that, despite its seemingly ephemeral quality, stored data like the kind at play in Microsoft Ireland is a physical thing that is quantitatively present in the foreign state. It is not truly any different than if the individual were being asked to obtain paper documents, or even tractors, from the foreign state.
Legally, the state’s power to compel the surrender of things — enforcement jurisdiction — is being extended into the territory of the foreign state, absent the latter’s permission and, in some circumstances, violating its laws. From a state responsibility point of view, it matters not that the courts or state entities issuing the compulsory orders are acting within their domestic jurisdiction and compelling entities that are within the issuing state’s territory, because the ultimate effect is extraterritorial; that is to say, the breach of the customary prohibition on extraterritorial enforcement occurs at the moment the data is gathered by the compelled entity on the foreign state’s territory and the compulsory order is consummated. The conduct is certainly attributable to the issuing state, since on any reasonable construction of the concept of agency the compelled individual is acting as the agent or proxy of the issuing state. This seems true whether the actors are properly considered to be the courts or the government and thus caught under Article 4 of the Draft Articles on State Responsibility or the compelled private individual itself, since it is under the direct control of the state and thus caught under Article 8. Footnote 121
As outlined in the first section of this article, this kind of behaviour has been considered objectionable by states since the pre-digital era. Notably, this is a kind of conduct that is not just viewed by states as being unfriendly but also as directly engaging their territorial sovereign interests, as can be seen by the various European reactions to the original Microsoft Ireland decision. As explained in the previous subsection, laws and practice at the state level can certainly be viewed as fractured, but given that international law is consent based, the most methodologically sound reaction to this situation is to revert to the more conservative, positivist position. The balance of the evidence points to the conclusion that states view this kind of compulsion as unlawful when it is directed at their territories. Accordingly, until a clearer or more nuanced picture emerges, in my view it is safe to conclude that a Microsoft Ireland-style warrant, if executed, breaches the rule against the exercise of extraterritorial enforcement jurisdiction.
Conclusions
As noted at the outset of this article, the goal here has been relatively modest. It has been to demonstrate that the issue raised in the Microsoft Ireland case has generated further controversy in an already fractured discussion about how transnational electronic evidence gathering can, does, and should proceed. It has also sought to demonstrate that while the dialogue on the issue has framed this as a law enforcement issue with international aspects, it is best understood as an international law problem that pertains to law enforcement. And it will be concluded here that the latter point is more than a semantic one, in that international law problems require international law solutions — solutions that, to be sure, can be aided by the adoption of technological solutions and by inter-law enforcement dialogue at every level, but because of the sovereignty concerns involved, must ultimately take the form of old-fashioned inter-state cooperation.
Much heat is being generated on this issue, particularly as both the Microsoft Ireland and Google Warrants cases wend their way through the American court system, but thus far there is little light, at least in terms of solutions gaining traction. Footnote 122 Clearly this is a problem that is in need of a solution. On the law enforcement side, there is clear indication that the MLAT system as it currently exists is simply inadequate for the task, and this inadequacy may be leading to more informal, even unlawful, actions by the police. From the point of view of individuals and civil society, without distinct rules around cross-border evidence gathering, procedural protections do not necessarily follow the investigative actions. People are more likely to be subject to prosecution as a result of these activities, but potentially less protected by human rights regimes, Footnote 123 not to mention the principle of legality. And the problem is as pressing as it is intractable. As the Council of Europe’s Cybercrime Convention Committee framed it in a 2014 report:
in the absence of an agreed upon international framework with safeguards, more and more countries will take unilateral action and extend law enforcement powers to remote transborder searches either formally or informally with unclear safeguards. Such unilateral or rogue assertions of jurisdiction will not be a satisfactory solution.
Furthermore, as victimisation grows, the public will ask why governments are not able to obtain data in a reasonable and legitimate way when lives are in danger and why justice frequently cannot be done. Footnote 124
In terms of what solutions might be generated, that is far beyond the scope of this article. However, to return to the jurisdictionalist paradigm invoked at the outset, I would venture that in international law terms this is a jurisdictional problem that is in need of a jurisdictional solution. As old-fashioned as it might seem, some form of treaty arrangement, probably at both the bilateral and multilateral levels, offers the most practical solutions. As noted above, there is activity on this front, and there will undoubtedly be more to come. Footnote 125 What is vital, perhaps, is the manner in which this international law problem is solved and, in particular, that it not be solved simply to smooth the way for law enforcement but, rather, in a way that is mindful of the various concerns at play. In a recent piece, Jennifer Daskal and Andrew Woods proposed a simple, but effective, set of principles that might guide these efforts, arguing that such cooperation should be undertaken in a way that accomplishes: (1) expedited and reciprocal access to data; (2) significant attention to human rights requirements; and (3) the embedding of transparency and accountability. Footnote 126 In terms of human rights protections, the Internet and Jurisdiction Project has proposed six “building blocks for fair process”: authentication, transmission, traceability, determination, safeguards, and execution. Footnote 127 Gail Kent has made quite detailed proposals for medium- to long-term solutions involving the creation of international agreements around data transmission regimes that harness technological tools and industry know-how. Footnote 128
Most recently, some of these proposals have seen active implementation in the form of the newly in force Agreement between the United States of America and the European Union on the Protection of Personal Information Relating to the Prevention, Investigation, Detection, and Prosecution of Criminal Offences, which seeks to provide a governing framework for cooperation between EU states and the United States on information transfers in the criminal context. Footnote 129 However, this is clearly not an easy effort, as even in the EU space the only consensus that has thus far been built is around a “Guidance Note” on transborder access to data under Article 32 of the Convention on Cybercrime. Footnote 130
There is no doubt that the nature of both electronic data and the Internet’s infrastructure present challenges to the operation and application of jurisdictional principles, particularly in the realm of enforcement, and this has put stress on that body of norms. Most of the literature in this area is geared towards figuring out essentially whether there is a “better way to do it,” and it may be that such a better way can evolve and perhaps is evolving. However, I would suggest that, while the landscape is rapidly changing, we are by no means in the middle of a Grotian moment in international law in regard to jurisdiction. Notwithstanding these challenges, states still do adhere to a Westphalian-bound model, where things are either here or there, inside or outside their territories. Those most pungent markers of state sovereignty — borders — are as they ever were. Despite the restless advancement of technology, when it comes to the exercise of enforcement jurisdiction, no new frontiers are yet emerging.


