Introduction
Information exchange is essential in the policy process because it constitutes fundamental structures of policy subsystems defined by a geographic scope, a topical policy area, and policy actors (Sabatier and Jenkins-Smith Reference Sabatier and Jenkins-Smith1993). Information, including knowledge, skills, and expertise, is considered the most basic and central resource for generating efficient policy outputs and changing policies (Ingold and Leifeld Reference Ingold and Leifeld2016). Information exchange involves more than merely acquiring or transmitting information from one actor to another in the subsystems. Interdependent actors gather technical and evidence-based information within and across coalitions to gain new understanding, enhance scientific knowledge, and reduce uncertainty and controversy in adversarial policy subsystems. They also exchange political and normative information within and across coalitions to exercise policy influence and choose advocacy venues and tactics (Weible and Sabatier Reference Weible and Sabatier2009; Leifeld and Schneider Reference Leifeld and Schneider2012). Such complex scientific and political information exchange becomes a critical parameter that fuels policy learning (Leifeld and Schneider Reference Leifeld and Schneider2012; May, Koski and Stramp Reference May, Koski and Stramp2016; Fischer, Ingold and Ivanova Reference Fischer, Ingold and Ivanova2017; Funke et al. Reference Funke, Huitema, Petersen and Nienaber2021; Nowlin Reference Nowlin2021).
Advocacy Coalition Framework (ACF) is one of the most sophisticated subsystem approaches to information exchange and policy learning within the policy process (Nowlin Reference Nowlin2021). The ACF specifies that policy actors having shared policy beliefs and resources form advocacy coalitions to translate their beliefs into policy changes within a subsystem. The policy beliefs and coalitions act as the filter through which information is exchanged (Henry, Lubell and Mccoy Reference Henry, Lubell and Mccoy2010; Henry Reference Henry2011; Matti and Sandström Reference Matti and Sandström2011; Henry, Dietz and Sweeney Reference Henry, Dietz and Sweeney2021). The ACF and broader literature addressing policy learning have primarily focussed on how two actors’ (i.e. dyadic) shared beliefs, similar characteristics, or positive symmetric relationships, such as reciprocal trust and collaboration, facilitate political and technical information exchange in collaborative policy subsystems (Leifeld and Schneider Reference Leifeld and Schneider2012).
However, information exchange between actors with different beliefs, dissimilar characteristics, or negative asymmetric relationships is not well understood. ACF literature widely assumes that convergence is the opposite of divergence (Henry Reference Henry2011). Yet, convergence (i.e. a tendency for actors to share information with similar others) and divergence (i.e. a tendency for actors to avoid exchanging information with dissimilar others) can also be distinct social processes (Henry Reference Henry2011; Weible et al. Reference Weible, Ingold, Nohrstedt, Henry and Jenkins-Smith2020), and in this case, how information exchange within and across coalitions occurs is not well known. Also, the characteristics and relationships of actors are frequently labelled the same because they are categorised into broad groups, but characteristics and relationships are not always “black and white.” They have varying degrees of similarities or differences. Furthermore, the lack of knowledge of one’s characteristics and relationships can often lead to misconceptions of where actors stand and a realisation that actors can, in fact, have asymmetric relationships (Matti and Sandström Reference Matti and Sandström2011).Footnote 1 These overlooked possibilities need to be addressed in examining the information exchange.
Also, there is open discussion among ACF scholars about how to conceptualise and measure coalitions, primarily relying on the measurement of shared beliefs in subsystems (Weible et al. Reference Weible, Ingold, Nohrstedt, Henry and Jenkins-Smith2020). We know how shared beliefs moderate or filter actors’ information exchange and infer intra- and inter-coalition information exchange. However, we do not know much about how coalitions have been created and developed, and then act as interconnected structures that empirically moderate or filter actors’ information exchange. To develop research in this area, we introduce the concept and measure of “identity-based subgroups” drawing from psychology literature: social identity (Tajfel and Turner Reference Tajfel, Turner, Austin and Worchel1979) and group entitativity (i.e. recognition of a social unit as a group) and self-categorisation theory (Campbell Reference Campbell1958; Turner Reference Turner1985). Identity-based subgroups refer to informal clusters consisting of two or more actors who recognise themselves as members of the cluster and share a common identity through the self-referential perception of similarities among actors (Campbell Reference Campbell1958; Lickel et al. Reference Lickel, Hamilton, Lewis, Sherman, Wieczorkowska and Uhles2000; Carton and Cummings Reference Carton and Cummings2012; Meyer et al. Reference Meyer, Glenz, Antino, Rico and González-Romá2014; Hornung, Bandelow and Vogeler Reference Hornung, Bandelow and Vogeler2019). Pre-existing group identity plays an essential role in shaping shared beliefs and building coalitions. Hornung et al. (Reference Hornung, Bandelow and Vogeler2019) suggest that social identity-based subgroups can act as the basis of forming individual beliefs and preferences, leading to coalitions when they are successfully mobilised and coordinated.
Identity-based subgroups and coalitions are different mainly because of (a) theoretical background, (b) glue binding them together, (c) relations to the beliefs, and (d) relations to the coalitions. Specifically, (a) conceptually, identity-based subgroups are drawn from the social psychology literature, including social identity (Tajfel and Turner Reference Tajfel, Turner, Austin and Worchel1979) and group entitativity and self-categorisation theories (Campbell Reference Campbell1958; Turner Reference Turner1985), which ACF literature has not much-paid attention to. (b) Identity-based subgroups are determined by the self-referent perception of similarities among actors, such as policy views, preferences (likes and dislikes), professional competencies, traits, and social roles. The subgroups capture the transition from individual to group identification (Campbell Reference Campbell1958; Lickel et al. Reference Lickel, Hamilton, Lewis, Sherman, Wieczorkowska and Uhles2000; Carton and Cummings Reference Carton and Cummings2012; Meyer et al. Reference Meyer, Glenz, Antino, Rico and González-Romá2014; Hornung, Bandelow and Vogeler Reference Hornung, Bandelow and Vogeler2019). Shared policy beliefs are treated as one of the major determinants. (c) Perceived similarities make actors see a group with social identity (Campbell Reference Campbell1958). Actors are not born with preset policy beliefs; an identity-based subgroup allows actors to learn and reinforce policy beliefs. The identity-based subgroup is a precursor for coalition building in a policy subsystem bounded by both a functional dimension (e.g. water and energy) and a territorial one (e.g. New York and California) (Sabatier and Weible Reference Sabatier, Weible and Sabatier2007; Hornung, Bandelow and Vogeler Reference Hornung, Bandelow and Vogeler2019). (d) Identity-based subgroups are cognitively delineated informal subdivisions of a larger group that may turn into a coalition shaped by primarily shared policy beliefs and functional coordination activities. For example, different social identities (e.g. religious identity differences) can transform social relations in a polarised adversarial policy system. Invoking common social identities (e.g. similar religious identities) can serve as powerful cues for promoting trust and cooperation among individuals, reshaping behavioural patterns, and influencing coalition building (Chu, Pink and Willer Reference Chu, Pink and Willer2021).
We aim to understand how technical and political information exchange is experienced depends on different identity-based subgroups, as a precursor to coalition building, in adversarial policy subsystems. Our primary research questions are: How does divergence in identity-based subgroups moderate the exchange of technical and political information between actors with various relationships in adversarial policy networks? Specifically, we look at three types of relationships: (1) trust, (2) collaboration, and (3) competition. Our study will provide insight beyond our traditional expectations about increasing political information exchange among actors having the same policy beliefs and cooperative or trustful relationships (Weible Reference Weible2008; Weible and Sabatier Reference Weible and Sabatier2009).
We focus on an adversarial local hydraulic fracturing (fracking) policy network in New York as a research context. Fracking is a well stimulation technique that involves drilling deep underground and injecting a mix of water and chemicals at high pressure into shale deposits to maximise shale gas extraction (Lee and Dodge Reference Lee and Dodge2019). While this technique allows extracting natural gas from basins considered too complicated or too costly to exploit previously, the ecological risks (e.g. contamination of surface waters and aquifers, methane emissions, or seismic activity) and scientific evidence of fracking’s economic and environmental impacts are contested and uncertain (Heikkila and Weible Reference Heikkila and Weible2017). This context results in political debates, divided political coalitions by shared policy beliefs, and considerable challenges to the regulation of fracking, displaying complicated political and technical information exchange patterns. The fracking policy represents an ideal case to examine political and technical information exchange in adversarial policy subsystems (Weible and Sabatier Reference Weible and Sabatier2009).
Information exchange, belief convergence, in adversarial policy subsystems
Information exchange refers to the complex processes of transferring and understanding tacit or explicit knowledge, skills, and expertise between policy actors so that one actor can perform various operations in subsystems or networks (Willem and Buelens Reference Willem and Buelens2007; Huang Reference Huang2014). Exchanging technical and political information is essential for coalition dynamics and vice versa. Information exchange contributes to policy learning and building stable coordination network relations that are critical for joint problem-solving capacities (Berardo and Scholz Reference Berardo and Scholz2010; Calanni et al. Reference Calanni, Siddiki, Weible and Leach2015).Footnote 2 The ACF is a crucial framework for the analysis of political and technical information exchange within and across coalitions created by a shared policy belief system comprising three belief categories: a deep core of fundamental normative and ontological axioms, a policy core of policy propositions and basic strategies, and a set of secondary aspects of instrumental decisions necessary to implement the policy core (Sabatier and Jenkins-Smith Reference Sabatier and Jenkins-Smith1999).Footnote 3
Previous ACF information exchange literature has investigated factors enabling or impeding information exchange within and across coalitions in the policy networks. Specifically, studies have examined the roles of informants and learning agents (e.g. policy brokers or policy entrepreneurs in subsystems) in bridging different beliefs and coalitions (Ingold Reference Ingold2011; Ingold and Varone Reference Ingold and Varone2012), convergence in characteristics between actors (e.g. policy belief, power, trust, collaboration) within and across coalitions (Henry, Lubell and Mccoy Reference Henry, Lubell and Mccoy2010; Koebele Reference Koebele2020), and information sharing outcomes (e.g. policy changes or shifting coalitions) (Sotirov and Winkel Reference Sotirov and Winkel2016). They found a significant role of scientific and technical information in modifying policy actors’ core or secondary beliefs and shifting coalitions and coalition members (Sabatier and Weible Reference Sabatier, Weible and Sabatier2007; Sotirov and Winkel Reference Sotirov and Winkel2016). A consensus from these studies is that crucial factors facilitating within-coalition information sharing include core belief convergence and strong, reciprocal relationships within coalitions (Moyson, Scholten and Weible Reference Moyson, Scholten and Weible2017).
However, existing scholarship overlooks the impacts of divergent characteristics or asymmetric relations on political and technical information exchange. ACF and broader literature addressing policy learning somewhat undertheorised the mechanism behind information exchange in the subsystems (Funke et al. Reference Funke, Huitema, Petersen and Nienaber2021; Nowlin Reference Nowlin2021). We know that similar characteristics or symmetric relations promote information exchange (Weible Reference Weible2008; Fischer, Ingold and Ivanova Reference Fischer, Ingold and Ivanova2017; Koebele Reference Koebele2020). However, the realisation that the seemingly same actors have divergent characteristics or relationships can hinder political and technical information exchange in adversarial networks, which has not been examined empirically (Henry Reference Henry2011). Divergent characteristics or asymmetric relations are prevalent across coalitions in networks, particularly adversarial networks (Henry Reference Henry2011; Lee and Lee Reference Lee and Lee2022; Matti and Sandström Reference Matti and Sandström2011). For instance, two collaborative actors (anti-fracking environmental activist groups and neutrally positioned local governmental actors) in adversarial subsystems may avoid exchanging scientific and technical information because of their different subgroup identities, blocking learning processes. A certain level of convergent characteristics or symmetric relations between actors may not be enough to overcome barriers to political information exchange when they show divergence of other kinds of characteristics or asymmetric relations in adversarial networks (Fischer et al., Reference Fischer, Ingold and Ivanova2017).
As one of the three types of policy subsystems (unitary, collaborative, and adversarial) coined by ACF, adversarial subsystems are characterised by minimal or asymmetric cross-coalition coordination interactions. Unitary policy subsystems or networks include one dominant coalition or a policy monopoly, and collaborative policy subsystems or networks involve cooperative coalitions where conflict is at intermediate levels (Weible Reference Weible2008). However, adversarial subsystems or networks share the following four features: “(1) competitive coalitions marked by polarised beliefs and minimal cross-coalitions coordination; (2) fragmented authority among governments or government agencies that are aligned with one of the competitive coalitions; (3) extensive venues shopping where coalitions seek an upper hand over rivals in any amiable venues; and (4) policy designs with clear winners and losers and little compromises” (Weible and Sabatier Reference Weible and Sabatier2009, 197). Compared to collaborative and unitary policy subsystems, adversarial subsystems involve diverse policy actors creating the networks’ structure and engaging in conflict. These attributes affect how technical information is politicised, how political information exchanges shape network structures, and how policy-oriented learning occurs within and across coalitions (Weible Reference Weible2008). Periods of policy gridlock in adversarial networks are often explained by the above four features (Kriesi and Jegen Reference Kriesi and Jegen2001; Weible et al. Reference Weible, Ingold, Nohrstedt, Henry and Jenkins-Smith2020). This study aims to extend current knowledge of coalition building and information exchange in ACF, focussing on how policy actors actively avoid exchanging information with those they perceive to have divergent characteristics or asymmetric relationships in adversarial subsystems.
Previous studies have distinguished between two types of information exchange in policymaking: technical and political information exchange. Both technical and political information are essential resources for policymaking. However, their information exchanges serve different purposes and reflect various interdependencies among actors (Leifeld and Schneider Reference Leifeld and Schneider2012). Technical or evidence-based information, often generated by scientists or policy analysts (information providers), allows policy actors to enhance their scientific information about the uncertain, complex problem (e.g. drilling techniques or potential risks for humans or the environment) (Fischer et al. Reference Fischer, Ingold, Sciarini and Varone2016; Ingold, Fischer and Cairney Reference Ingold, Fischer and Cairney2017). Instrumental use of technical information promotes intra-coalition and inter-coalition learning in collaborative subsystems. However, the political use of technical information, presumably, across-coalitions, could be high in adversarial systems. Political information concerns the strategic exchange of information about policy beliefs, tactics in venue shopping, and material and social resources; thus, it shapes the political behaviours of policy actors such as coordination, organisation, and mobilisation (e.g. joint lobbying activities or alliance formation) (Leifeld and Schneider Reference Leifeld and Schneider2012). Sharing more sensitive political information is more likely to occur within coalitions than between competing coalitions due to differences in core beliefs and high levels of competition across coalitions. The technical and political information flows are broadly decided by various political contexts, such as unitary, collaborative, and adversarial subsystems or networks (Weible Reference Weible2008). There are nuanced differences in the expected pattern of political and technical information exchange in an adversarial policy network. Revealing factors affecting technical and political information exchange in adversarial networks is crucial for the progress on controversial policy issues, coalition-building processes, and policy changes (and stability) in networks comprising diverse actors with competing interests.
Antecedents of information exchange in adversarial policy subsystems or networks
The literature on information exchange in ACF indicates that belief convergence, high trust, and collaboration promote information exchange within and across coalitions in policy subsystems or networks, while the effect of competition on information sharing is debatable. However, coalitions in the subsystems are not sufficiently conceptualised and empirically measured (Weible et al. Reference Weible, Ingold, Nohrstedt, Henry and Jenkins-Smith2020), limiting our knowledge of intra- and inter-coalition information exchange in the ACF. Drawing from social identity (Tajfel and Turner Reference Tajfel, Turner, Austin and Worchel1979) and group entitativity and self-categorisation theory (Campbell Reference Campbell1958; Turner Reference Turner1985), we posit that an identity-based subgroup conceptually spots actors’ cognitive clusters based on perceived similarities among actors, serving as the precursor of beliefs and preference formations. It also empirically captures coalition-building processes. We examine how different identity-based subgroups are associated with information exchange between actors with previously identified antecedents in adversarial networks.
Belief convergence and advocacy coalition
The three-tiered belief systems (deep, core, and secondary policy beliefs) shared among policy actors in networks are the basis for advocacy coalition formation and coordination (Sabatier and Jenkins-Smith Reference Sabatier and Jenkins-Smith1999; Weible and Sabatier Reference Weible and Sabatier2009; Henry, Lubell and Mccoy Reference Henry, Lubell and Mccoy2010). While scholars continue to disagree on the ways to define and measure advocacy coalitions, advocacy coalitions refer to informal alliances of policy actors aligned around common beliefs or values about a policy issue (Weible and Ingold Reference Weible and Ingold2018; Weible et al. Reference Weible, Ingold, Nohrstedt, Henry and Jenkins-Smith2020). They were originally defined as “consisting of policy actors who share policy core beliefs and coordinate their behaviour in nontrivial ways over extended periods of time toward some sort of shared outcome in a policy subsystem” (Weible et al. Reference Weible, Ingold, Nohrstedt, Henry and Jenkins-Smith2020, 7). In the fracking policy subsystems in Texas, New York, and Colorado, Heikkila and Weible (Reference Heikkila, Weible, Weible, Heikkila, Ingold and Fischer2016) identified two coalitions: the pro-fracking coalition that prefers to see fracking expanded or continued and the anti-fracking coalition that prefers to see it stopped or limited.
Policy actors with shared belief systems are more likely to exchange information and similarly interpret evidence (Weible Reference Weible2008; Fischer, Ingold and Ivanova Reference Fischer, Ingold and Ivanova2017; Koebele Reference Koebele2020). Shared core beliefs lead actors to form coalitions in the networks and strengthen information sharing among members within the same coalitions. Shared secondary beliefs also promote information exchange within the coalitions and help actors devise specific policy solutions through information exchange. However, information exchange between actors with different secondary beliefs can lead to shifts in beliefs and coalitional membership (Koebele Reference Koebele2020). Thus, as Sabatier and Weible (Reference Sabatier, Weible and Sabatier2007) noted, coalitions tend to “filter out information that suggests that the deep core or policy core beliefs of their coalitions may be invalid and/or unattainable, and regard coalitions with contrasting policy beliefs as less trustworthy and more powerful than they actually are” (Olsson Reference Olsson2009, 172). However, these observations are made based on the erroneous assumption that belief similarities create coalitions, and coordination within coalitions would automatically follow (Satoh, Gronow and Ylä-Anttila Reference Satoh, Gronow and Ylä-Anttila2021).
Trust
Policy actors tend to choose technical and political information exchange partners from trusted sources in adversarial policy networks (Carpenter, Esterling and Lazer Reference Carpenter, Esterling and Lazer2004). Trust refers to a psychological “willingness to become vulnerable to another based on confident, positive expectations of the other’s conduct” (Lewicki Reference Lewicki, Schneider and Honeyman2006, 191). Trust plays a crucial role in selecting and being selected as information exchange partners because trust prevents opportunistic behaviours (Berardo and Scholz Reference Berardo and Scholz2010; Huang Reference Huang2014; Lefebvre et al. Reference Lefebvre, Sorenson, Henchion and Gellynck2016). Also, based on transaction economics and social capital theories, information from trusted actors is more likely to be viewed as reliable and accurate. Perceived trustworthiness enables policy actors to disclose and exchange sensitive information with candour, thereby allowing them to reduce the concealment of useful information (Lubell Reference Lubell2007; Calanni et al. Reference Calanni, Siddiki, Weible and Leach2015). For instance, two highly trusted anti-fracking grassroots and regional environmental organisations shared their political strategies and joint lobbying activities (Ingold, Fischer and Cairney Reference Ingold, Fischer and Cairney2017).
Collaboration
Policy actors rely on technical and political information sources from existing collaborative contacts in adversarial policy networks (Fischer, Ingold and Ivanova Reference Fischer, Ingold and Ivanova2017). Embeddedness theorists (Polanyi Reference Polanyi1944; Granovetter Reference Granovetter1985; Uzzi Reference Uzzi1997) recognise that actors involved in economic transactions are typically embedded in socially attached relationships. Policy actors are embedded within a network to the extent that they have a strong record of repeated transactions with other actors (Lee and Lee Reference Lee and Lee2018). This is also true for information exchange networks. Embeddedness in collaboration networks enables two actors to develop regular interactions, familiarity, and trust, increasing the likelihood of voluntary disclosure of knowledge assets and deficiencies (Polanyi Reference Polanyi1962; Berardo and Scholz Reference Berardo and Scholz2010). Embeddedness in collaboration is likely to create a strong motivation for the information sources to help out and for the recipients to seek help from embedded relationships (Carpenter, Esterling and Lazer Reference Carpenter, Esterling and Lazer2004). Relying on existing collaborative contacts should be particularly important in adversarial fracking networks where policy actors are in conflicts of interests between economic promotion, landscape and natural resource protection, and unaware of other actors’ political strategies and behaviours (Fischer et al., Reference Fischer, Ingold, Sciarini and Varone2016; Ingold, Fischer and Cairney Reference Ingold, Fischer and Cairney2017). Effective transfer of political and technical information requires revealing the sources’ proprietary knowledge and the recipients’ willingness to learn. Informal voluntary collaboration increases motivation to learn and share (Carpenter, Esterling and Lazer Reference Carpenter, Esterling and Lazer2004).
Competition
Policy actors such as governments, businesses, and nonprofits are embedded in both collaboration and competitive relationships in adversarial policy networks (Lee and Lee Reference Lee and Lee2018, Reference Lee and Lee2022; Lee and Dodge Reference Lee and Dodge2019), affecting how actors share technical and political information throughout the network. Uzzi (Reference Uzzi1997) further developed embeddedness theory by suggesting that arm’s length or competitive ties could help overcome the limitations of embeddedness, such as having excessive social obligation or when cohesion hinders rational decisionmaking. The existing literature is ambivalent about the impact of competition on information exchange. On the one hand, competition between actors is negatively associated with information sharing (Botelho Reference Botelho2019). Actors may want to protect critical information from leaking and sustain competitive advantages by not sharing information with competitors (Botelho Reference Botelho2019). On the other hand, competitors can serve as an essential source for innovative ideas and new technical information; thus, actors want to discover what their competitors think and know so that they can benchmark themselves and form winning strategies (Tsai Reference Tsai2002; Lee and Dodge Reference Lee and Dodge2019).
Given that competition has these two contradictory effects on information exchange, we posit that the influence of competition on information exchange is likely to vary depending on identity-based subgroups and different types of information in adversarial networks. For example, in adversarial fracking networks, competing policy actors in rival subgroups or coalitions (e.g. pro-fracking landowners’ associations versus anti-fracking environmental activist groups) can be more hesitant to exchange political information. They may want to share new expert-based technical information to fortify the legitimacy of their political position and dampen the mobilisation of potential opponents (Weible, Pattison and Sabatier Reference Weible, Pattison and Sabatier2010; Lundin and Öberg Reference Lundin and Öberg2014).
Social identities, information exchange, filtering effect
Social identity theory (Tajfel and Turner Reference Tajfel, Turner, Austin and Worchel1979) and group entitativity and self-categorisation theory (Campbell Reference Campbell1958; Turner Reference Turner1985) account for the positive link between identity-based subgroups and shared beliefs, views, and behaviours of subgroup members in policy subsystems (Hornung, Bandelow and Vogeler Reference Hornung, Bandelow and Vogeler2019). At the same time, they explain how split identities between subgroups lead to policy actors’ divergent beliefs, views, and behaviours in the subsystems (Hornung, Bandelow and Vogeler Reference Hornung, Bandelow and Vogeler2019). Identity-based subgroups are formed when a set of policy actors are perceived as sharing a common identity through cognitive, evaluative, and affective self-categorisation processes. These processes occur through the self-referential perception of similarities among actors, including policy views, preferences (likes and dislikes), professional competencies, traits, and social roles, and capture transition from individual to group identification (Campbell Reference Campbell1958; Lickel et al. Reference Lickel, Hamilton, Lewis, Sherman, Wieczorkowska and Uhles2000; Carton and Cummings Reference Carton and Cummings2012; Meyer et al. Reference Meyer, Glenz, Antino, Rico and González-Romá2014; Hornung, Bandelow and Vogeler Reference Hornung, Bandelow and Vogeler2019). As Campbell (Reference Campbell1958) noted, perceived similarities make actors see a group with a social identity. Actors are not born with preset policy beliefs, and an identity-based subgroup allows actors to experience and learn policy beliefs. The identity-based subgroup serves as a precursor for coalition building in a policy subsystem. Identity-based subgroups capture actors’ cognitive map reflecting in-group homogeneity and out-group heterogeneity among them before they are mobilised into coalitions. Identity-based subgroups are cognitively delineated informal subdivisions of a larger group that may turn into a coalition.
Policy actors in the subsystems tend to define themselves (self-concept) based on their perceived identity-based subgroups (e.g. circles of friends, ethnic groups, religious groups, and political groups) (Carton and Cummings Reference Carton and Cummings2012; Hornung, Bandelow and Vogeler Reference Hornung, Bandelow and Vogeler2019; Hornung and Bandelow Reference Hornung and Bandelow2020). This tendency affects the ways policy actors believe, think, and behave because identity-based subgroups fulfill several basic social and political needs, such as belonging, distinctiveness, and access to power and resources (Van Bavel and Pereira Reference Van Bavel and Pereira2018).
Furthermore, the social grouping and self-categorisation processes among identity-based subgroups account for how and why social comparisons transform self-perception, influence intergroup differences relative to intragroup differences, and introduce biases to intergroup relations (Willem, Scarbrough and Buelens Reference Willem, Scarbrough and Buelens2008; Abrams and Hogg Reference Abrams, Hogg, Dovidio, Hewstone, Glick and Esses2010; Zhang and Guler Reference Zhang and Guler2020). An actor’s cognitive map representing how policy actors are classified and how many identity-based subgroups exist in the subsystem (e.g. environmental activist groups, landowners’ associations, and industry groups in the case of fracking policymaking processes) can activate categorisation salience and out-subgroup bias (Tajfel and Turner Reference Tajfel, Turner, Austin and Worchel1979; Turner Reference Turner1985). The subjective dividing lines splitting a network into several identity-based subgroups may play an overlooked role in structuring technical and political information flows in the network. Previous studies have shown that policy actors use political ideology-based social subgroups as essential lenses to process information (Dokshin Reference Dokshin2016). For example, during the early stages of the gas boom, members of landowners’ associations in NY identified themselves as “Friends of Natural Gas” and emerged as strong supporters and information sources about gas development in communities (Dokshin Reference Dokshin2016).
The perceived divergence of identity-based subgroups facilitates within-subgroup assimilation via pressure to conform to the in-subgroup’s norms. Identity-based subgroups strengthen inter-subgroup bias by positively assessing actors’ in-subgroup relative to out-subgroup (Leaper Reference Leaper and Benson2011). Identity-based subgroups produce and reproduce policy actors’ political beliefs and judgments, such as support for specific policy options or political resistance to particular policy issues. This idea is related to ACF because coalitions are likely to result from a type of informal subgroups with a particular subgroup identification, based on shared policy beliefs and preferences by subgroup members in the policy subsystems (Hornung, Bandelow and Vogeler Reference Hornung, Bandelow and Vogeler2019; Hornung and Bandelow Reference Hornung and Bandelow2020). ACF explains the role of biased assimilation within coalitions relying on the measurement of shared beliefs in policy learning (Hornung, Bandelow and Vogeler Reference Hornung, Bandelow and Vogeler2019). Also, since coalitions in adversarial policy networks represent intense conflicts and prefer to win without compromise (Weible and Sabatier Reference Weible and Sabatier2009), inter-coalition bias is more likely to occur when selecting and using political information sources in adversarial policy networks.
Different identity-based subgroups are assumed to decrease information sharing between subgroups in adversarial networks. Different identity-based subgroups also moderate the link between dyadic relations (e.g. trust, collaboration, competition) and information exchange. Before engaging in information exchange in adversarial networks, policy actors consider the types/strengths of their connections and subgroups they identify with. Faultlines derived from identity-based subgroups provide the impetus for policy actors to differentiate themselves and potentially divide into diverse subgroups within the networks despite their existing favourable relations (Lau and Murnighan Reference Lau and Murnighan1998; Bezrukova et al. Reference Bezrukova, Jehn, Zanutto and Thatcher2009). Such a divide limits collective information sharing and policy learning processes (Lau and Murnighan Reference Lau and Murnighan1998; Bezrukova et al. Reference Bezrukova, Jehn, Zanutto and Thatcher2009). For example, when two actors have low trust levels, they are less likely to exchange information if they also have different subgroup identities. When high levels of conflict and polarised beliefs arise in the adversarial networks, policy actors strive for trusted, in-group sources to exchange political information and protect their strategies (Burt Reference Burt1992; Carpenter, Esterling and Lazer Reference Carpenter, Esterling and Lazer2004). Actors may be less likely to share critical political information or tend to hoard sensitive political information with out-group members, despite their collaborative connections. Different identity-based subgroups may eliminate the benefit of sharing information with trusted, out-subgroup members. Also, social subgroup identities are considered to be the basis of a policy actor’s belief and preference formation in subsystems (Hornung, Bandelow and Vogeler Reference Hornung, Bandelow and Vogeler2019). Thus, the perception of different identity-based subgroups by actors may lead to variations in the ways they exchange information and learn (Hornung, Bandelow and Vogeler Reference Hornung, Bandelow and Vogeler2019). Examining how divergent identity-based subgroups play a role in information exchange can present a valuable contribution to the ACF research on coalition formation and development and knowledge sharing processes. We suggest the following hypotheses about moderating effect of different identity-based subgroups on the associations between social relationships and information exchange:
H1a: When two policy actors’ identity-based subgroups are different, trust is associated with reducing technical information exchange in adversarial policy networks.
H1b: When two policy actors’ identity-based subgroups are different, trust is associated with reducing political information exchange in adversarial policy networks.
H2a: When two policy actors’ identity-based subgroups are different, collaboration is associated with reducing technical information exchange in adversarial policy networks.
H2b: When two policy actors’ identity-based subgroups are different, collaboration is associated with reducing political information exchange in adversarial policy networks.
H3a: Two policy actors’ different identity-based subgroups moderate the relationship between competition and technical information exchange in adversarial policy networks.
H3b: Two policy actors’ different identity-based subgroups moderate the relationship between competition and political information exchange in adversarial policy networks.
In all, Figure 1 illustrates our research model. We will examine the moderating effect of different identity-based subgroups (see the dashed lines in the model).

Figure 1. Conceptual model.
Methods
Study context: local hydraulic fracturing policy in New York state
Our case is an adversarial policy subsystem or network related to oil and gas development using fracking in a mid-size city situated in the Southern Tier region of New York. This city is dominated by agricultural production, with some tourism-related outdoor sports and wineries, yet it has experienced an economic decline for decades. The possibility of developing natural gas in New York through fracking with horizontal drilling emerged around mid-2007 as oil and gas companies were aggressively leasing acreage in the Southern Tier region adjacent to Pennsylvania (Wilber Reference Wilber2012). This local fracking policy subsystem is embedded in the larger state political system characterised by home rules, politically liberal “blue” state, and individualistic political culture, which structures the general operation of politics and policymaking (Morgan and Watson Reference Morgan and Watson1991; Weible and Ingold Reference Weible and Ingold2018). New York state political system is typically depicted as an individualistic political culture where individuals and groups advance their self-interest through political actions, political parties are strong and held considerable power, and government serves specific interests (Morgan and Watson Reference Morgan and Watson1991). While New York’s existing regulations were unfavourable to shale gas development, lawmakers quickly passed a critical bill in 2008 to make issuing permits for shale gas wells easier, and the Governor signed the bill into law. “At that time, looking at neighbouring Pennsylvania, the industry assumed that drilling permits would be issued without much interference from State environmental regulators” (Simonelli Reference Simonelli2014, 260). But, in 2018, the Governor declared a de facto moratorium and ordered the New York Department of Environmental Conservation (DEC) to review the generic environmental impact of fracking. Since then, an anti-fracking movement grew rapidly, and grassroots groups in individual townships emerged (Simonelli Reference Simonelli2014; Dokshin Reference Dokshin2016). In the state as a whole, the controversy split both the public and policymakers, who either advocated against fracking based on scientific information and political claims of water contamination and other environmental destruction or advocated for it based on its economic potential and technical evidence. Pro- and anti-fracking stakeholders sought to influence local government policymaking, relying on New York’s tradition of strong home rule. Anti-fracking grassroots stakeholders’ engagement in municipal meetings influences local elected officials’ policy decisions (Arnold and Neupane Reference Arnold and Neupane2017). Over 177 local governments, including our case, banned or placed a moratorium on fracking and challenged the state’s authority to override home rules on energy extraction in 2014 (Council of State Governments 2017). Local bans fragmented the state political landscape into smaller, economically undesirable units and influenced Governor Cuomo’s decision to ban fracking at the state level in 2014.
The selected fracking policy case has the four features of an adversarial policy subsystem or network suggested by Weible and Sabatier (Reference Weible and Sabatier2009) and is situated in the spectrum of adversarial subsystems. Specifically, first, the network had competing coalitions and conflicts marked by polarised policy beliefs and fragmented authority between diverse actors (Heikkila and Weible Reference Heikkila and Weible2017; Weible Reference Weible2018). For instance, most landowners’ associations were pro-fracking, and claimed that the local government’s control contributed to a confusing legal patchwork of regulations. In contrast, several anti-fracking environmental organisations argued that the only way to protect the residents from the risks of fracking was to ban it through the local government’s regulations, citing irreversible impacts of fracking on communities. These different policy beliefs created competing subcoalitions and divided authority within the network. Second, there was controversy over scientific and technical knowledge related to health impacts, water quality, job creation, and economic opportunities for local businesses (Heikkila and Weible Reference Heikkila and Weible2017). For example, landowners’ associations and local environmental groups presented their unique and contradicting scientific analyses of fracking’s effects on health and economic issues (Dodge and Lee Reference Dodge and Lee2015). Third, lawsuits associated with high levels of distrust and heated disputes over local government’s control over fracking activities were involved (Heikkila and Weible Reference Heikkila and Weible2017; Berardo et al. Reference Berardo, Holm, Heikkila, Weible, Yi, Kagan, Chen and Yordy2020). The city council and the local executive government collaboratively passed a fracking moratorium at one point. In response, a local landowners’ association, an oil and gas company, and small business owners jointly sued a local elected official over the decision, arguing that it was superseded by the Oil, Gas, and Solution Mining Law. This legal case on moratorium decisions has stimulated heated disputes about the locus of control over fracking activities since 2011. Lastly, key policy actors shared a winner-take-all mentality (Weible and Sabatier Reference Weible and Sabatier2009; Weible, Heikkila and Pierce Reference Weible, Heikkila and Pierce2018). On the surface, this mentality centered the discussion on one solution: whether the local governments should issue setback requirements or zoning ordinances regarding fracking activities.
Policy network boundary specification
An initial step in conducting a social network analysis of a policy network involves determining which actors to include in the network. This study used a three-step network specification method in the “realist” tradition outlined by Laumann, Marsden and Prensky (Reference Laumann, Marsden and Prensky1983). Rather than using researcher-defined criteria – the “nominalist” approach (Laumann, Marsden and Prensky Reference Laumann, Marsden and Prensky1983) – the realist approach uses informants to identify network members. We used a three-stage process to specify the boundaries of the fracking policy network. First, we compiled a “naïve” list of 37 organisations that had the potential to be influential members of the fracking policy network, using searches of newspaper articles, government documents, reports, and web documents. Second, we recruited four central informants from the naïve universe to make additions to the original list.Footnote 4 The four informants were asked to rate each listed organisations’ policy influence, using a five-point Likert scale. Eleven organisations below the break-point were removed.Footnote 5 Lastly, during semi-structured interviews, we asked each organisation if any organisations were omitted or deleted from the list. The county legislature was deleted from the 26 potential policy actors because it had only a tangential interest and influence in decisionmaking. Thus, the final population included 25 organisations, such as landowners’ associations, media, business associations, environmental civic organisations, and governmental agencies (see Appendix 1).
Data collection and data analyses
From July to September 2014, we surveyed by semi-structured interviews, 18 out of 25 actors involved in the fracking network, equalling a response rate of 72%. The seven nonresponding actors included the city legislature, city legal department, two regional business associations, an environmental organisation, and two state-wide oil and gas associations. They were missing at random depending on policy actors’ goals over fracking, levels of policy influence, or trust as assessed by others. We used a dyadic reconstruction process to address the missing data. This process is generally accepted when analysing network data with nonrespondents (Stork and Richards Reference Stork and Richards1992). We used 544 respondents-identified dyads among 25 policy actors to test our hypotheses. Key stakeholders included environmental, civic organisations, oil and gas industry associations, landowners’ associations, city agencies, and council. Each interview had a set of quantitative social network surveys and open-ended interview questions and lasted 90 minutes on average. For this study, quantitative network survey data was used to examine under what situations network actors exchange their technical and political information about fracking policy design and implementation with others. We collected the following directional (counting a tie when one side in the dyad reported the presence of the tie), relational data: technical information exchange, political information exchange, trust, collaboration, competition, and identity-based subgroups.
First, for technical information exchange, we provided respondents with the list of policy actors. We then asked them to indicate in the past 12 months (1) from which actors they obtained scientific, technological, or technical information related to fracking (0 = no and 1 = yes), and (2) to which actors they provided scientific, technological, or technical information related to fracking (0 = no and 1 = yes). We combined their responses by summing up one-way sending and receiving ties to create a network of technical information exchange.
Second, for political information exchange, we asked respondents to indicate how frequently they communicate with other actors to discuss fracking policy per year for all dyads using a seven-point scale (0 = never, 3 = quarterly, and 6 = daily) (Laumann and Knoke Reference Laumann and Knoke1987). Based on their answers, a network of political information exchange was created.
Third, trust was operationalised by “confident, positive expectation regarding another’s conduct (e.g. words, actions, and decisions) that is related to the city’s hydraulic fracturing policy” (Lewicki Reference Lewicki, Schneider and Honeyman2006). We asked respondents to rate their perceived levels of trust for each policy actor on the network list on a scale from one to five (1 = does not trust at all, 3 = trust moderately, 5 = trust extremely). Their answers were used to create a network of trust between actors. We included the trust network as a control variable in the model and introduced the interaction term between trust and different identity-based subgroups to examine whether perceived different identity-based subgroup membership moderates the influence of trust on technical/political information exchange.
Fourth, collaboration was operationalised as whether or not an actor “works side-by-side and actively pursues opportunities to work together as an informal team (i.e. attempt to find ways to work together but do not establish a formal agreement or contract, ‘in the spirit of collaboration’) with other actors” (Harris et al. Reference Harris, Luke, Burke and Mueller2008). With the same list of actors, respondents were asked to indicate with whom they collaborated during fracking policymaking processes (0 = no and 1 = yes). This allowed us to create a network where a tie (1) represents collaboration, whereas the absence of tie (0) represents no collaboration. We included the collaboration network as a control variable in the model and introduced the interaction term between collaboration and different identity-based subgroups to examine whether perceived different identity-based subgroup membership moderates the influence of collaboration on technical/political information exchange.
Fifth, competition was measured by directly asking respondents whether or not they compete with others on the same list to achieve their organisational goals (0 = no and 1 = yes). This information was used to create a network of competition between actors. We used the collaboration network as a control variable, but this variable was dropped in models 2 and 4 because of the high correlation with Different identity-based subgroups × Competition (r = 0.991, p < .01). Our model introduced the interaction term between competition and different identity-based subgroups to examine whether perceived different identity-based subgroup membership moderates the influence of competition on technical/political information exchange.
Sixth, identity-based subgroups are operationalised by an actor’s recognition of a social unit as a group based on the similarity of group members to each other (Lickel et al. Reference Lickel, Hamilton, Lewis, Sherman, Wieczorkowska and Uhles2000; Cruwys et al. Reference Cruwys, Steffens, Haslam, Haslam, Jetten and Dingle2016; Bentley et al. Reference Bentley, Greenaway, Haslam, Cruwys, Steffens, Haslam and Cull2020). It was measured by directly asking respondents to classify the listed actors into various groups based on the following question: “Could you sort the listed organisations into groups according to how similar they are?” We verbally clarified that respondents could create as many groups as they think similar to one another during the semi-structured interviews. Our measure of subgroup identity—intuitive systems of self-classification by participants in the group sorting task—is theoretically driven by social identity (Tajfel and Turner Reference Tajfel, Turner, Austin and Worchel1979) and group entitativity and self-categorisation theories (Campbell Reference Campbell1958; Turner Reference Turner1985). This measure is empirically validated by previous psychology studies (Lickel et al. Reference Lickel, Hamilton, Lewis, Sherman, Wieczorkowska and Uhles2000; Cruwys et al. Reference Cruwys, Steffens, Haslam, Haslam, Jetten and Dingle2016; Bentley et al. Reference Bentley, Greenaway, Haslam, Cruwys, Steffens, Haslam and Cull2020). Specifically, our respondents-sorting survey approach is derived from the study of groups at the center of social psychology, highlighting social group salience, group membership and support, and group compatibility. The group-sorting method in which participants are asked to sort a given list of organisations into distinct groups based on perceived similarity has received robust validation in psychology (Lickel et al. Reference Lickel, Hamilton, Lewis, Sherman, Wieczorkowska and Uhles2000; Cruwys et al. Reference Cruwys, Steffens, Haslam, Haslam, Jetten and Dingle2016; Bentley et al. Reference Bentley, Greenaway, Haslam, Cruwys, Steffens, Haslam and Cull2020). These experimental studies found that the group-sorting method has robust internal consistency and good convergent and discriminant validity. Cruwys and colleagues (Reference Cruwys, Steffens, Haslam, Haslam, Jetten and Dingle2016, 635) also noted that this participatory social identity sorting/mapping method provides a novel framework and approach for data generation that has some of the strengths of qualitative and quantitative approaches. Data collected through the sorting/mapping process are readily quantified and easily subjected to standard statistical analysis. However, the experience of completing the sorting/mapping process has similarities with semi-structured qualitative procedures because “participants are able to generate idiographic responses (maps) as they see fit and in ways that are self-exploratory, self-created, and empowering – even enjoyable.” Our question allowed respondents to consider the extent to which they observe similarities among in-group members and differences between out-group members (see also Carton and Cummings Reference Carton and Cummings2012; Hornung et al. Reference Hornung, Bandelow and Vogeler2019). Also, subgroup identification through self-categorisation shows how actors internalise subgroup prototypes that describe other actors’ identities, beliefs, perceptions, and behaviours in the policy network (Hogg, Abrams and Brewer Reference Hogg, Abrams and Brewer2017). In addition, Hornung and colleagues (Reference Hornung, Bandelow and Vogeler2019) noted that social identities measurement applicable to policy studies is primarily tested and validated in psychology. They encouraged research on social identities in the policy process and measurement advancement in policy studies (For a further detailed explanation, please see Hornung et al.’s (Reference Hornung, Bandelow and Vogeler2019) Table 1 on page 217). Similarity-based sorting approach is finding its way in policy studies, for example, Gilad and Alon-Barkat’s (Reference Gilad and Alon-Barkat2017) research on senior managers’ social identification with the participants of large-scale social protests in 2011 and motivation for policy change in Israel.
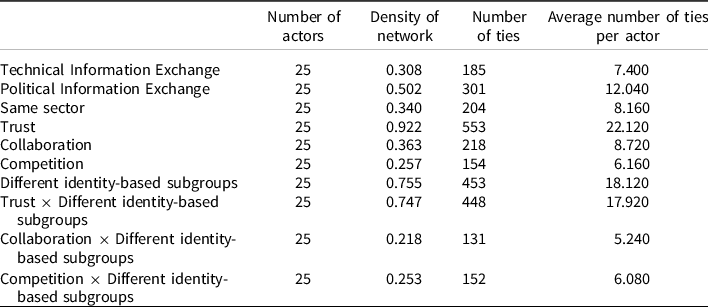
Table 1. Comparative statistics for technical and political information networks
In this sense, based on their self-classification of subgroups, we created an identity-based subgroups network and then transformed it into a different identity-based subgroups network because of our research interests in divergent processes in the policy subsystems. The different identity-based subgroups network indicates that a tie between two actors (1) represents a different identity-based subgroup membership, whereas the absence of a tie between two actors (0) means the same identity-based subgroup membership.Footnote 6 Our model included the different identity-based subgroups (to control its main effect on technical and political information exchange) and interaction terms between different identity-based subgroups and network embeddedness.Footnote 7
Lastly, we included same sector as a control variable in the model to control for the effects of homophily (a tendency that similarity in actors’ background increases their chances of interaction among actors) (Mcpherson, Smith-lovin and Cook Reference Mcpherson, Smith-lovin and Cook2001). Sectoral affiliation shapes a common view on certain policies and policy preferences, affecting policy processes (Hornung, Bandelow and Vogeler Reference Hornung, Bandelow and Vogeler2019; Hornung and Bandelow Reference Hornung and Bandelow2020). We asked respondents to indicate their sectoral types, such as public, nonprofits, and private sectors. This allowed us to create the same sector network where a tie (1) represents the same sector, whereas the absence of tie (0) means a different sector.
Analysis
We used the quadratic assignment procedure (QAP) multiple regression in UCINET to test the moderating effects of different identity-based subgroups between network embeddedness and technical/political information exchange. As we are primarily interested in the role of an exogenous covariate-divergent identity-based subgroups-to model the information exchange structures, we chose QAP as our modelling tool. Also, as Cranmer et al. (Reference Cranmer, Leifeld, McClurg and Rolfe2017) noted, QAP is the most accessible, well implemented, and easy to interpret, compared to the ERGM that is prone to numerical instability in the estimation processes. QAP regression overcomes the problem inherent in network data, of autocorrelations of errors (Dekker, Krackhardt and Snijders Reference Dekker, Krackhardt and Snijders2007). Policy network actors respond to a relational question with reference to one another, which violates the statistical independence assumption in standard inferential tests (Krackhardt Reference Krackhardt1988).
QAP regression for this study treats a directional, dyadic relationship (existence or absence of a tie between two actors) as a unit of analysis and proceeds in two steps to explain the nonindependent network data. First, ordinary least square (OLS) regression coefficients are calculated in the usual manner. Second, a null hypothesis reference distribution of regression coefficient and R squared values is generated, against which the observed coefficients (from the first step) can be compared to determine their statistical significance. To create this reference distribution, QAP randomly permutes all the rows and matching columns of the dependent matrix. This step is repeated 2,000 times to estimate a reference distribution of regression coefficient and R squared values (Borgatti, Everett and Johnson Reference Borgatti, Everett and Johnson2013).
We used the Double-Dekker Semi Partialing (DDSP) method, which is particularly robust to autocorrelation problems. This approach is also robust to the effect of collinearity, that is, correlation among the independent variables in QAP multiple regression (Dekker, Krackhardt and Snijders Reference Dekker, Krackhardt and Snijders2007). Standardised regression coefficients for independent variables and interaction terms in QAP can be interpreted identically to those in OLS regression (Bell and Zaheer Reference Bell and Zaheer2007).
Results
We examined both technical and political information exchange among 25 actors involved in the fracking policy. Table 1 reports the descriptive statistics of dependent and independent variable networks, and Figure 2 represents the networks’ visualisation. The political information exchange network exhibits a higher density (0.502, implying that 50.2% of all possible connections exist in the network) than the density of the technical information exchange network (0.308). The correlation between political and technical information exchange is 0.526. Both networks are positively associated with trust and collaboration networks (see Appendix 2). As individualistic New York’s political culture and style indicated (Morgan and Watson Reference Morgan and Watson1991), the comparison between the two densities suggests that fracking policy actors tend to focus on forming political coalitions or developing political strategies to advance their political interests and exercise their influence more than gathering or providing scientific information in regulatory policymaking.Footnote 8 One plausible explanation is that policy actors from different identity-based subgroups may have already been actively engaged in collaborative processes politically mandated or encouraged by local governments, creating a higher level of political communication than technical communication in adversarial networks. Also, our network visualisations demonstrate that policy actors’ information exchange patterns are organised according to their sectoral memberships, and the political information network seems to show more cross-sectoral exchange than the technical information network (see correlation coefficients between variables in Appendix 2).
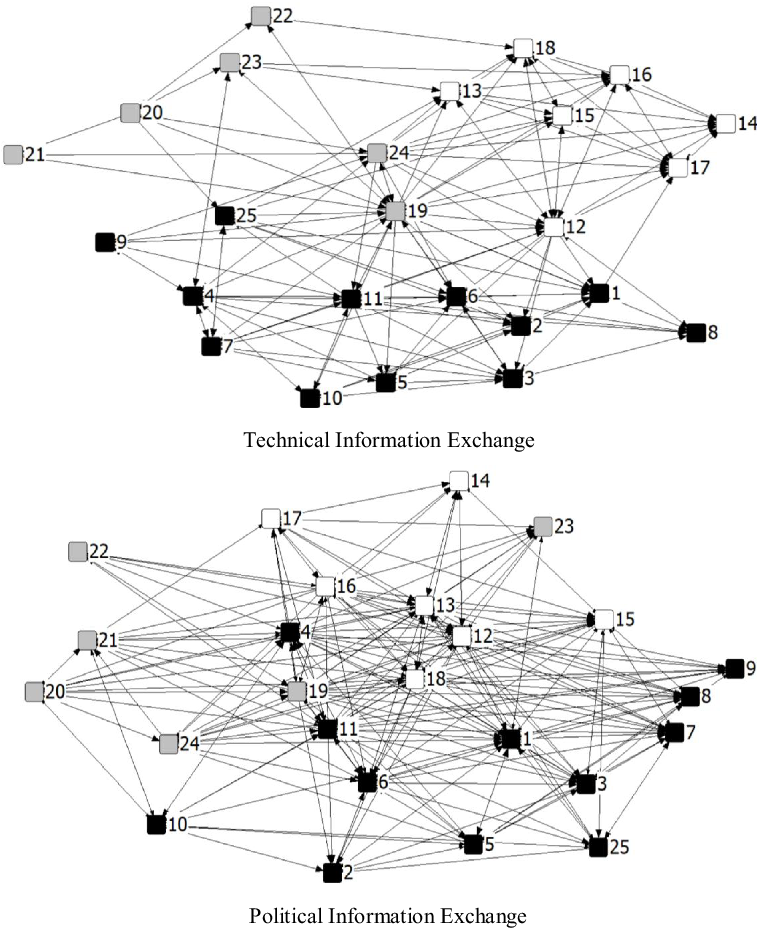
Figure 2. Visualisations for Technical and Political Information Networks.
Note: Line: existence of relationships, Colour: black-private sector; white-nonprofit sector; gray-public sector, Number: actor ID.
Table 2 shows the QAP multiple regression analysis results, presenting standardised coefficients for independent and control variables to show their relative importance on two types of information exchange and adjusted R 2 . We dropped Competition because of the high correlation with Different subgroup identity × Competition (r = 0.991, p < 0.01; see Appendix 2). For the control variables, the results indicate that same sector is positively and significantly associated with technical and political information exchange (p < 0.01). Trust and collaboration are positively and significantly associated with technical and political information exchange, respectively.
Table 2. Results of QAP multiple regression
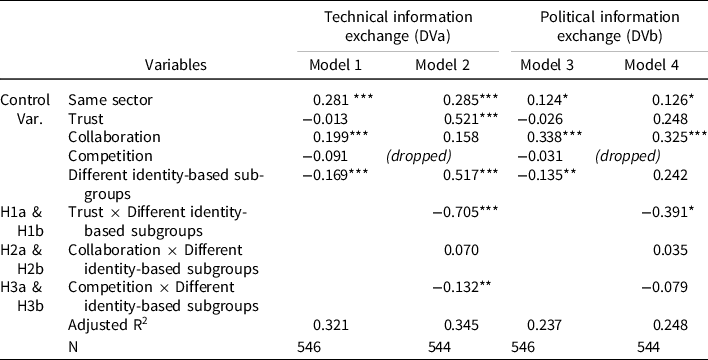
Dependent variable: technical and political information exchange at dyads among 25 policy actors
* p < .10;
** p < .05;
*** p < .01.
Regarding our first three sets of hypotheses (H1a & b, H2a & b, H3a & b), we added three interaction effects in Model 2 to examine the moderating effects of different identity-based subgroups on the relationships between relational embeddedness (trust, collaboration, and competition) and information exchange. The results show that the coefficients on Trust × Different identity-based subgroups are negative and significant for technical information exchange (p < 0.01) and political information exchange (p < 0.10).
Also, the interaction term between collaboration and different identity-based subgroups is not statistically significant, indicating that different identity-based subgroups may not moderate the association between collaboration and political information exchange, not supporting H2a and b (see Model 4). This is somewhat unexpected. Given the fact that relying on existing collaborative contacts is critical in political information flows in the adversarial network (see the positive and significant coefficient on collaboration at the 0.01 level in Model 4), a plausible explanation is that collaborative relationships may already capture homogenous group identities. Or, since policy actors from different identity-based subgroups had already been actively engaged in collaborative governance processes mandated or encouraged by local governments, different identity-based subgroups may not restrict the information exchange between collaborative actors.
Our model also introduced an interaction term between competition and different identity-based subgroups and examined whether the effect of competition was more salient for actors with different subgroup identities. The coefficient for this interaction term is negative and statistically significant for technical information exchange (p < 0.05), providing support for H3a. In other words, competing policy actors in different subgroups (e.g. landowners’ association versus environmental activist group) are less likely to exchange their expert-based technical information to protect critical information from leaking and sustain their competitive advantages (Botelho Reference Botelho2019).
Discussion and conclusions
Information exchange is a basic, essential part of advocacy coalition and policy processes, weaving subsystem structures that influence policy actors’ strategic behaviours and policy change. Informed by social identity theory, group entitativity, and self-categorisation theory, we introduced the concept of identity-based subgroups that are the basis of individual beliefs and preferences and serve as precursors to coalition building. We examined information exchange within and across identity-based subgroups in the subsystems (Hornung, Bandelow and Vogeler Reference Hornung, Bandelow and Vogeler2019). We showed the links between the divergence of identity-based subgroups and technical/political information exchange in an adversarial network (Hornung, Bandelow and Vogeler Reference Hornung, Bandelow and Vogeler2019).
First, we found that the strong positive association between trust and technical information exchange became negative among actors perceived as members of different subgroups in the adversarial fracking network. Trust may not necessarily help different subgroup actors overcome technical information transfer challenges due to the network’s fragmented group identities. An actor’s cognitive map about how policy actors are classified serves as an information filtering mechanism that strengthens out-subgroup bias and can affect secondary beliefs on specific policy solutions. This, in turn, can impede technical information flows among trusted policy actors across subgroups (Hornung, Bandelow and Vogeler Reference Hornung, Bandelow and Vogeler2019). Actors in one subgroup may also withhold information from trusted actors from another subgroup because they are reluctant to violate their own subgroup’s expectations or damage the in-subgroup relationship by talking to the opposing side in an adversarial network. According to the social identity, group entitativity, and self-categorisation literature, the perception of being part of the same identity-based subgroup provides actors with motivations for information exchange during the policy process (Hornung, Bandelow and Vogeler Reference Hornung, Bandelow and Vogeler2019). It also gives a subgroup member a cognitive framework reference that allows information transfer and integration to be productive and mutually beneficial to subgroup members (Willem, Scarbrough and Buelens Reference Willem, Scarbrough and Buelens2008; Zhang and Guler Reference Zhang and Guler2020). An actor’s intention to choose information sources is influenced by both trusting relationships and social expectations from in-subgroup members. In the face of cognitive dissonance associated with trusting out-subgroup members, actors may cope with the situation by reducing information exchange with trusted actors who do not share subgroup membership.
Second, different identity-based subgroups between two policy actors exacerbate the negative effects of competition on technical information exchange, which can lead to information concealment in adversarial networks. Competition is seen as both (1) a key inhibitor of cross-subgroup and cross-coalition information exchange and (2) a source for innovative ideas and new information in adversarial networks (Botelho Reference Botelho2019). Beyond the previously identified mixed findings on the role competition plays in information exchange, this study highlights that the decision to limit technical information exchange between competitors can be explained by divergence in subgroup identities. Specifically, policy actors can choose not to provide the competing subgroup actors in the network with evidence-based, technical information because they believe that the benefits of information withholding are far greater than social costs, such as being punished by the subgroup members or losing political allies in adversarial policy subsystems or networks. Withholding information can help policy actors maintain their power or advantages within subgroups in the networks. For instance, the anti-fracking environmental civic organisation in the fracking network maintained competitive relations with the municipal government’s economic development department. The organisation chose to conceal its technical information from the economic development department. This organisation may have feared ruining the existing cooperative alliances and losing their political positions in the network. Our findings suggest that sharing technical information across subgroups can be strategically selective and politicised in adversarial networks.
Third, there are different underlying divergent network dynamics and factors that determine the extent to which technical and political information is shared in adversarial policy networks, when focussing on different subgroup identities as the basis of policy core beliefs and preference formation for coalition building (Hornung, Bandelow and Vogeler Reference Hornung, Bandelow and Vogeler2019). Technical and political information serve different purposes in coalition building and policy processes. Technical information enables policy actors to collect scientific expertise about a contested social phenomenon, problems, and solutions, whereas political information is exchanged to exercise political influence and coordinate actions and strategies among actors (Fischer, Ingold and Ivanova Reference Fischer, Ingold and Ivanova2017). We show that different identity-based subgroups influence the exchange of technical information more than political information in adversarial networks. Taken together, these findings point to a more contingent account of different types of information exchange. Our findings provide empirical evidence to support Weible’s (Reference Weible2008) proposition about the political use of expert-based information across coalitions in adversarial policy networks. High-stake conflicts in adversarial networks make technical information appealing as a political weapon to argue against opposing coalitions. We also suggest that technical information exchange across identity-based subgroups may change policy actors’ core or secondary beliefs and thus shift coalitions and coalition members (Sabatier and Weible Reference Sabatier, Weible and Sabatier2007; Sotirov and Winkel Reference Sotirov and Winkel2016).
Finally, our study demonstrates why policy actors reduce sharing or hide information from others in adversarial networks by focussing on how different identity-based subgroups affect technical and political information exchange. As shown in many adversarial policy networks, excessive information hoarding or withholding could lead to costly lawsuits. One of the goals of lawsuits is court-mandated evidence and information sharing through the pretrial discovery process. To solve the problems with information hoarding behaviours in adversarial networks, an aspiring policy coordinator or entrepreneur (typically a governmental actor or elected official) in the networks (Ingold and Leifeld Reference Ingold and Leifeld2016) needs to consider creating opportunities for informal collaboration between diverse subgroups and coalitions. The policy coordinators can develop a shared definition of a problem and search for the commonality of the identities that these subgroups exhibit. Psychological safety, defined as a climate in which people feel safe to take interpersonal risks in a team or an organisation (Edmondson Reference Edmondson2019), such as discussing problems or differences with peers without fear of retribution, is a relevant concept for information flows inside adversarial networks with diverse subgroup identities. Group faultlines inside contentious networks may result in fear of punishment over risky information sharing across coalitions. Training on sharing and safeguarding technical and political information with external policy experts or partners is one way to increase psychological safety for policy actors in adversarial networks. Also, policy actors can learn from information sharing successes and failures in their own and other networks (Cuganesan, Hart and Steele Reference Cuganesan, Hart and Steele2017).
Beyond the significance of our findings in adversarial policy networks, we also suggest that different identity-based subgroups may matter for political and technical information exchanges between competitors in collaborative subsystems. Competition for resources or politics leading to intentional competition for reputation among different groups also exists in collaborative subsystems with low levels of conflict. Also, collaborative subsystems can shift to adversarial subsystems depending on the levels of conflicts among actors or political systems where subsystem is embedded, and vice versa (Weible Reference Weible2008). Two policy actors’ different identity-based subgroups can deteriorate the relationship between competition and technical information exchange in collaborative policy networks.
While our findings provide novel insights into the moderating effects of different identity-based subgroups on the association between relational embeddedness and information sharing, many compelling questions remain. Our findings are limited by a cross-sectional single observable adversarial network and the survey method. Future research is needed to clarify the dynamic trajectory of technical and political information exchange in adversarial networks by employing a longitudinal multiple case study and mixed methods. For instance, does information exchange contract over time as actors in adversarial networks learn more about others’ positions and draw sharper boundaries between “us” and “them” as conflict progresses? Is this dynamic the same for technical and political information exchange, or do these two types of exchanges show divergent trajectories as policymakers attempt to weigh evidence (technical information) and different subgroups seek to influence decisions on normative grounds (political information)? Also, future research needs to clarify how identity-based subgroups evolve within and across coalitions empirically and then compare information exchange within/across identity-based subgroups and within/across coalitions in policy networks. For example, such a dynamic empirical approach will enable us to assess whether identity-based subgroups or coalitions are more or less decisive about political information exchange compared to technical information exchange. In addition, findings in this research can be compared to other types of policy subsystems or network settings, such as collaborative subsystems and unitary subsystems (Weible Reference Weible2008). This could reveal, for example, that technical and political information might flow more easily through collaborative or unitary subsystems compared to adversarial ones. In doing so, future studies can provide a more comprehensive understanding of the roles different identity-based subgroups play in information exchange in subsystems.
Supplementary material
To view supplementary material for this article, please visit https://doi.org/10.1017/S0143814X22000228
Data availability statement
Replication materials are available in the Journal of Public Policy Dataverse at https://doi.org/10.7910/DVN/EMDNSQ





