Article contents
Collecting relations for the number field sieve in 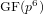 $\text{GF}(p^{6})$
$\text{GF}(p^{6})$
Published online by Cambridge University Press: 26 August 2016
Abstract
In order to assess the security of cryptosystems based on the discrete logarithm problem in non-prime finite fields, as are the torus-based or pairing-based ones, we investigate thoroughly the case in 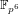 $\mathbb{F}_{p^{6}}$ with the number field sieve. We provide new insights, improvements, and comparisons between different methods to select polynomials intended for a sieve in dimension 3 using a special-
$\mathbb{F}_{p^{6}}$ with the number field sieve. We provide new insights, improvements, and comparisons between different methods to select polynomials intended for a sieve in dimension 3 using a special- 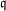 $\mathfrak{q}$ strategy. We also take into account the Galois action to increase the relation productivity of the sieving phase. To validate our results, we ran several experiments and real computations for various polynomial selection methods and field sizes with our publicly available implementation of the sieve in dimension 3, with special-
$\mathfrak{q}$ strategy. We also take into account the Galois action to increase the relation productivity of the sieving phase. To validate our results, we ran several experiments and real computations for various polynomial selection methods and field sizes with our publicly available implementation of the sieve in dimension 3, with special- 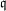 $\mathfrak{q}$ and various enumeration strategies.
$\mathfrak{q}$ and various enumeration strategies.
Information
- Type
- Research Article
- Information
- LMS Journal of Computation and Mathematics , Volume 19 , Special Issue A: Algorithmic Number Theory Symposium XII , 2016 , pp. 332 - 350
- Copyright
- © The Author(s) 2016
References
- 11
- Cited by

